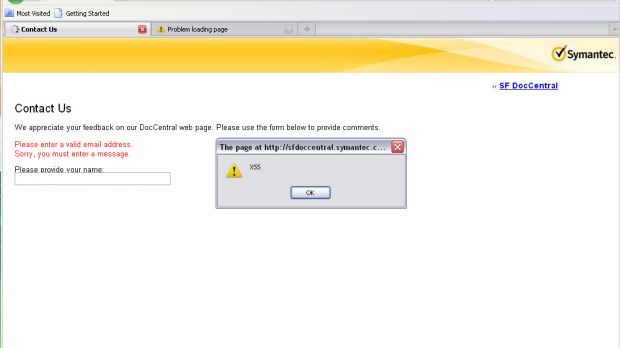
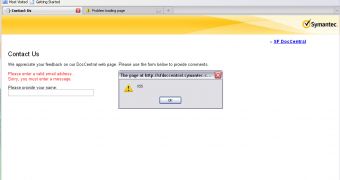
Security researcher Prakhar Prasad has identified cross-site scripting vulnerabilities on a number of three subdomains owned by security solutions provider Symantec. Fortunately, the company has addressed the issues before they could be exploited by cybercriminals.
The subdomains affected by the flaw were clientui-kb.symantec.com, sfdoccentral.symantec.com, and engweb.symantec.com.
“These issues are dangerous because they can be used to steal cookies or hijack Symantec users' accounts. Even worst they can be used to launch client-side exploits, for instance browser exploits by inserting malicious JavaScript code in the XSS payload which can completely take over a person's computer,” Prasad told Softpedia.
We’ve asked the expert to describe a simple scenario in which an attacker leverages these security holes against unsuspecting internauts.
“For a simple exploitation, an attacker can construct a URL containing the XSS payload then post it in Symantec forums or send to a user via an email. To deter suspicion the attacker can use URL shortening services like bit.ly, goo.gl, etc. that may ultimately steal cookies or initiate client-side exploits when viewed by the victim,” he explained.
Symantec did acknowledge for Softpedia the existence of the vulnerabilities and promised to fix them as soon as possible, which they did. However, there were some communication issues and the researcher is unhappy with the fact that it’s so difficult to report vulnerabilities to such a major company.
Just like many other security experts who have found themselves in the same situation, he calls out to organizations, asking them to provide means for proper vulnerability reporting.
“I'm pretty unhappy the way they dealt with my issue, they didn't reply to my email. I even tried to contact them on their Twitter account (@symantec) but got no reply. Now when it seems they have fixed their vulnerabilities, they haven't informed me about it,” Prasad said.
“They should make some policies regarding responsible disclosure on their web services. For a reputed security solutions company like Symantec, this incident was completely unexpected.”
 14 DAY TRIAL //
14 DAY TRIAL //