Over the past period, we’ve heard about numerous malware attacks in which cybercriminals signed their creations with valid digital certificates in an effort to ensure they remained undetected. Symantec experts have analyzed how the attackers manage to steal private keys by relying on malware.
Experts explain that it’s almost impossible for a cybercriminal to manually go through every compromised computer to check if it has private keys of valid digital certificates.
However, they can turn to pieces of malware that can easily retrieve the valuable data from an infected device.
The most common pieces of malware that accomplish this task are Backdoor.Beasty, Infostealer.Snifula, Downloader.Parshell, Trojan.Spyeye, W32.Cridex, W32.Qakbot, Infostealer.Shiz, Trojan.Carberp and Trojan.Zbot (aka ZeuS).
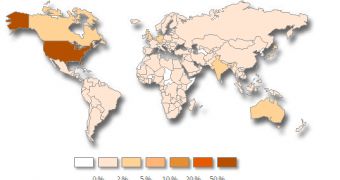
Most of these malicious elements have been spotted on computers located in the United States.
So how does malware extract digital certificates?
Usually, digital certificates are kept in Windows’ certificate store. From here, they can be extracted by using functions such as PFXExportCertStoreEx. In order to export the private key as well, the function is called with the EXPORT_PRIVATE_KEYS option.
This function exports the information to a .pfx file, which is often encrypted by cybercriminals.
Most pieces of malware start stealing digital certificates as soon as the computer is started, but some of them wait for the attacker’s command.
Once they gain access to private keys, cybercriminals can sign their creations by using freely-available tools such as “Sign Tool.”
In order to avoid losing their private keys, organizations are advised to keep them on a network that’s separated from the company’s internal network. In addition, developers should use test certificates during production.
It’s not recommended for digital certificates and private keys to be stored on computers. They should be locked in a safe, stored on IC cards, USB tokens, or hardware security modules. If that’s not possible, they should at least be archived and protected with a strong password.
Finally, experts advise organization to avoid as much as possible storing them on portable media.
 14 DAY TRIAL //
14 DAY TRIAL //