Following the disclosure of a flaw in a section of the Symantec website that allegedly allows for SQL injection attacks, the company has denied its existence and invoked an "inconsistent exception handling routine for language options." The Romanian hacker who disclosed the vulnerability disagrees and has released additional proof to back up his claims.
The Romanian ethical hacking group known as HackersBlog documented an SQL injection attack against the emea.symantec.com website yesterday. The vulnerability was disclosed by a member of the group, going by the nickname of "Unu" (Someone), who specified that he contacted Symantec on the matter.
In a response to the security group, which was also published on HackersBlog, the renowned security vendor claimed that "Upon thorough investigation, we have determined that the Blind SQL Injection is, in fact, not effective. The difference in response between valid and injected queries exists because of inconsistent exception handling routine for language options."
In an e-mail to us, a Symantec representative confirmed the same scenario. "The issue was not in fact a hack, and did not expose a vulnerability, simply an error message," she said. Although, she also added that "We're grateful to 'Unu' for highlighting this to us."
The security group appreciated Symantec's cooperation and response and pointed out that "This could help other organisation[s] see and understand that the best way to approach things is by open communication and dialog." However, "Unu" is not happy with the explanation. "I left room for a response from Symantec out of fair play... but this does not mean that I also have to agree with what they claim," the hacker wrote (translated from Romanian).
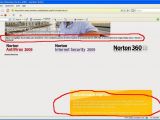
Furthermore, in order to prove that it was indeed an SQL injection, "Unu" published and explained two more screenshots. According to him, he was able to count the table columns after executing, though the URL, order by column SQL commands. Therefore, when trying order+by+2 there was no error and the text on the page remained intact. However, when executing order+by+3, an error occurred, because there was no third column to order by, and the text on the page disappeared.
This led the hacker to conclude that there were only two columns in the table and that the commands were executed against a real database. Symantec confirmed for us that "No company or customer information was exposed," but "Unu" pointed out that this was only because the UNION function had been disabled, this also being the reason why this attack was a blind SQL injection and not a regular one.
The Symantec spokeswoman who contacted us explained that "Upon notification of the potential vulnerability, Symantec immediately took the site down, conducted comprehensive testing and determined that the issue is not a security vulnerability." However she also underlined that the company "has addressed this issue and the web page is back up and running."
Note: In light of the new evidence submitted by "Unu," we have requested additional clarifications from the security vendor and we are awaiting a reply from the agents responsible with handling this incident. Please stay tuned for an update on this page. Update: We have received an update from Symantec as a result of our latest inquiry. A spokesperson informed us that "Symantec has investigated the reported SQL issue and maintains that it was not a security vulnerability. However, as part of our standard security precautions and best practices, Symantec is conducting a larger review of the webpage."
"The page has been taken down while it’s currently under review. This is part of our standard investigation process. Symantec is committed to ensuring that the webpage is secure and takes any potential security issues very seriously," the representative also stresses.

 14 DAY TRIAL //
14 DAY TRIAL //