The latest variant of Dyre/Dyreza banking Trojan comes with an expanded list of targets that includes financial institutions in Switzerland, and it is pushed to the victim computers through a Windows vulnerability seen to be employed by cyber-espionage group Sandworm.
The Trojan is delivered through spam emails that include a PowerPoint attachment containing an exploit for the CVE-2014-4114 vulnerability in Windows operating system. The weakness is present in the OLE (Object Linking and Embedding) packager that allows download and execution of INF files.
OLE is the technology that facilitates sharing of data between different programs and it is integrated into Microsoft Office components.
Researchers at the Danish security consultancy firm CSIS observed that the Dyre version distributed through the recent email campaign comes with an updated list of targets in the configuration file, including banks in Switzerland.
Stealing financial details is what Dyre has been created for, as it can be leveraged in man-in-the-middle (MitM) attacks that intercept communication between the client and the bank without raising suspicion to either party.
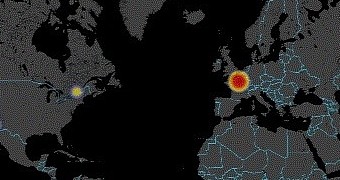
According to the researchers, this particular version of the malware establishes communication with a host located in France, Peter Kruse from CSIS says in a blog post.
The malware appears to have gained popularity in the cybercriminal circles, as it has been leveraged in multiple attacks lately.
 14 DAY TRIAL //
14 DAY TRIAL //