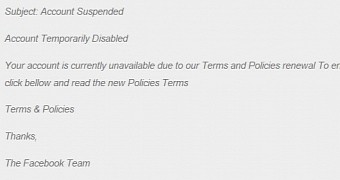
Emails purporting to be from Facebook and claiming that the recipient’s account has been temporarily disabled have been observed in the wild distributing a link to a malicious file.
Cybercriminals often rely on this theme as a lure since there is a high chance that the recipient of the message has a Facebook account and would be interested in the modification added to the social network platform.
Malicious file poses as PDF file
In this case, the reason claimed for the alleged account suspension is a renewal of the terms and policies document.
Facebook does make changes to its policies but these are signaled once the user logs into their account in order to make sure that the new terms enjoy the desired visibility and are not lost in the email feed.
The malicious message floating on the web includes a link where the user can access the new information. However, according to OTA, it points to a file hosted on assetdigitalmarketing[.]com, a domain that may have been compromised by the cybercriminals, or it may have been set up by them specifically for malware distribution.
The downloaded file has a double extension (TermsPolicies.pdf.exe), masquerading as a PDF file that has the appropriate icon appended, but a closer look reveals the true nature of the item, which is in fact an executable.
The scam has an increased rate of success on Windows systems where file extensions are not visible because it would appear as a legitimate PDF.
Antivirus protection should prevent infection
An analysis of the malware on VirusTotal reveals that most popular antivirus products have the necessary signatures to detect it.
Checking the developer metadata in the properties section of the file shows that the crooks used it in the past as a fake update for Java.
Once installed, TermsPolicies.pdf.exe may attempt to steal sensitive information itself and deliver it to a remote server or it can funnel in other malware pieces.
OTA does not specify the address the malicious message came from, but the fake communication is signed by “The Facebook Team.” Verifying if the sender information is in tune with the type of the message is a good way to spot a scam.
Also, it is recommended to take a look at the domain hosting the file offered for download. Generally, an entity hosts on its infrastructure data delivered to its clients. Getting an item from a website unrelated to the purported sender should be considered suspicious.
 14 DAY TRIAL //
14 DAY TRIAL //