The internal system in eBay for exchanging messages between traders contains a stored cross-site scripting (XSS) vulnerability that could lead to session hijacking; it was reported to the company more than one year ago and continues to be unpatched.
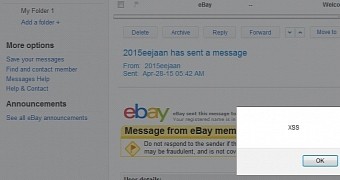
Jaanus Kääp, a penetration testing expert from Clarified Security, found that an attacker could send someone on eBay a malicious JavaScript payload by abusing the photo upload feature of the service.
Session cookies can be hijacked
The expert discovered that two GET parameters (“picfile” and “X-File-Name”) of the photo upload request can be modified to include the JavaScript code before reaching the targeted recipient.
Kääp says that after making these changes and passing the verification gates such as captcha, he intercepted the request once more and also modified the file name. He is not sure that this step is essential for the success of the attack, though.
When the victim opens the message, the malicious script is executed automatically. The risk for the recipient is that their eBay session cookies can be stolen by the attacker, who can then have access to the entire profile and impersonate the rightful owner.
No HttpOnly flag for session cookies
The expert notes in a blog post on Tuesday that the HttpOnly flag is not present in the HTTP response header for all the session cookies in eBay.
This flag is optional and blocks access to the sensitive cookie through client-side scripts. If present, it could help mitigate XSS risks.
“Only 3 cookies are HTTPonly in ebay, none of them are needed for session hijacking,” Kääp writes.
An analysis of the vulnerability revealed that the filename was used in two places inside the HTML message, and it was properly encoded only in one of them, thus leaving the possibility to add arbitrary JavaScript code in the second.
Patching may not be as easy as it looks
Fixing the flaw is a simple matter of adding encoding, but this change may impact other parts of the code and cause malfunctions, Kääp said via email.
However, taking more than a year for solving this problem is unusually long and it is the reason why the pentester decided to make a public disclosure.
Testing the weakness was done with Firefox, but it works regardless of the web browser. According to the expert, he first reported it to eBay in December 2013 and the last contact with the company regarding this matter occurred in September 2014.
Kääp said that each time he sought a status update (about three times), eBay informed him that they would not provide any details about when or how the issue would be fixed.
 14 DAY TRIAL //
14 DAY TRIAL //