A few hours ago, US authorities revealed that 24-year-old Russian national Aleksandr Andreevich Panin pleaded guilty to conspiracy to commit wire fraud and bank fraud, and admitted developing and distributing the notorious SpyEye banking Trojan.
Experts from Trend Micro have been assisting authorities with their investigation for the past four years.
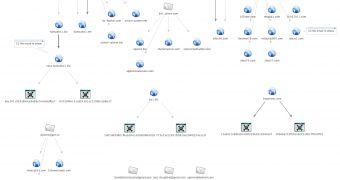
“Over the intervening period, we mapped out the infrastructure used to support the malware, we identified weak points in that infrastructure and pursued a number of important leads pointing to the identities of individuals behind this pernicious banking Trojan,” Trend Micro’s Rik Ferguson explained in a blog post.
Ferguson revealed that Panin made some rookie mistakes while he was selling SpyEye to cybercriminals. Researchers found that he often used very weak passwords such as “loveme,” “kissme” and “Danny000.″
Trend Micro Senior Threat Researcher Loucif Kharouni revealed that Panin and his accomplice, Algerian man Hamza Bendelladj, had often inadvertently disclosed information that ultimately led to authorities identifying them.
Email addresses, Jabber numbers, ICQ numbers, and websites found in forum posts and malware configuration files helped investigators in tracking down Panin and Bendelladj.
“While Panin believed that he was very good at hiding his tracks, it’s now obvious that he wasn’t as good as he thought he was. Around the time he was selling SpyEye, he also became very sloppy and not particularly careful; despite using multiple handles and email addresses, Trend Micro, working together with the FBI, found his real identity,” Kharouni said.
Panin will be sentenced in April 2014. He was arrested in July 2013 while passing through an airport in Atlanta.
In October 2013, when Ross William Ulbricht was arrested for allegedly operating Silk Road, the FBI revealed that he also made some rookie mistakes, which led to him being identified.
 14 DAY TRIAL //
14 DAY TRIAL //