Two weeks ago, visitors on spin.com music news website who did not have the latest patches for the browser plug-ins could have fallen victim to a drive-by download attack that seeped in RIG exploit kit (EK).
As soon as the EK discovered a vulnerable plug-in (Java, Silverlight and Flash Player), it would take advantage of an available vulnerability to download malicious software on the affected computer. Two of the malware pieces detected by security researchers at Symantec are Dyre and ZeuS Trojan (also known as Zbot).
Unpatched software opens the door to cyber-attacks
Dyre has been spotted in multiple malicious campaigns, being delivered mostly via email. It is known for its ability to intercept browser communication with websites for certain financial institutions and stealing banking credentials.
According to the researchers, the bad code was discovered on the website on October 27, and at the moment there is no information about the amount of time it was available, or the number of visitors whose computers fit the bill to be infected.
However, the online location is quite popular and telemetry data from Symantec revealed that the malicious campaign was mainly targeted against visitors from the US.
Several vulnerabilities have been observed to be leveraged by the exploit kit, some of them allowing actions that would prevent its detection on some systems.
The crimeware would rely on exploiting two use-after-free security glitches in Internet Explorer, along with flaws in unpatched versions of Adobe Flash Player, Silverlight and Java.
Most of the weaknesses are from 2013, and one of them had been disclosed in 2012; this means that really careless users were affected by the malicious campaign.
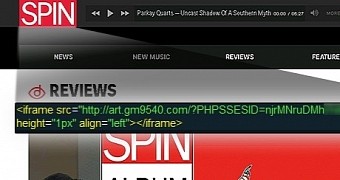
Website's code has been cleaned of the malicious iframe
The page hosting RIG EK was heavily obfuscated, Ankit Singh of Symantec says in a blog post on Tuesday, and before it starts exploiting vulnerabilities in browser plug-ins, RIG checks for the presence of certain antivirus products.
The campaign continues only if the security product is not present on the machine. As far as the payload is concerned, Singh observed both Dyre banking Trojan (also known as Dyreza) and a variant of ZeuS. In both cases, XOR cipher is used to avoid detection of the malware.
Currently, spin.com has been cleaned off the bad code and users should no longer be at risk when visiting it.
RIG exploit kit has been employed to infect computers connecting to compromised Drupal websites through the recent SQL injection vulnerability. The same behavior of enumerating the security products before downloading the payload was observed in those cases, too.
 14 DAY TRIAL //
14 DAY TRIAL //