Researchers keep discovering new things about the attacks that targeted major South Korean organizations last week.
South Korean antivirus company AhnLab has revealed that in some cases, the attackers abused their patch management systems to push malware. However, according to experts from F-Secure, it appears that spear phishing emails have also been utilized.
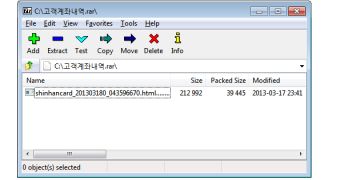
F-Secure researcher Broderick Aquilino reports that they’ve uncovered a malicious archive whose name translates into “The customer’s account history.”
In this archive, they have found a file that was entitled “shinhancard_2103231_0343342,” Shinhan being the name of one of the targeted financial institutions.
This piece of malware was created on March 17, just a few days before the organizations have reported disruptions.
Experts also highlight the fact that in the case of the wiper malware observed in the attacks, not all systems need to get infected. That’s because some wiper variants are capable of deleting data from remote systems by utilizing credentials found in the configuration files of SSH clients.
 14 DAY TRIAL //
14 DAY TRIAL //