Spamhaus announced that the Domain Block List has been added new information designed to provide increased protection not just against spam but other types of threats, too.
The Domain Block List (DBL) is a database containing domains pulled from spam messages. It is updated in real time and administrators can implement it into email server software to scan the message body of an email in order to identify, classify or reject spam.
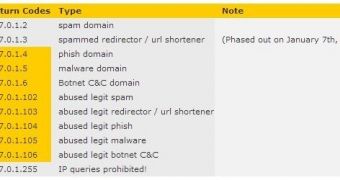
Two new data sets, resulting from several months’ worth of work, will be added to the DBL, aiming at domain names linked to spreading malware, “droppers” in particular, and command and control servers for botnets.
The reasoning is simple: a user accessing these domains can get their machine infected or they could already be infected and receive commands from the remote server.
Through the information provided in the first set, the Domain Block List will be able to both prevent malware from reaching a clean machine and identify infected systems running malicious software, “through the use of a DNS Response Policy Zone.” It is similar to the Spamhaus Botnet Controller List, but the focus is on the domain names.
The second set covers “legitimate domains hosting websites that have been compromised or otherwise abused by spammers,” the Spamhaus post says.
Spammers could try to compromise websites and thus take advantage of the good reputation of domains and IP addresses in order to extend their life time or payloads.
This can be achieved through outdated versions of widespread Content Management System (CMS) packages, Joomla and WordPress being among the targets. A simple file on a legitimate website can easily redirect the audience to a spam-serving address.
Starting July 1, 2014, Spamhaus will add the new return codes from the DNSBL (DNS-based Blackhole List) to all mirrors and administrators will be able to use them to benefit from the new information. The company makes available a complete list of the DBL return codes.
Spamhaus warns that even if most server email applications should have no problem working with the new return codes, some of them may need to be configured to accept them.
“Administrators using DBL return code data should note the replacement of 127.0.1.3 for spammed redirector / url shortener domains with 127.0.1.103. We are making this change so that people who prefer to treat the new 'abused legit' listings differently than dedicated spam, malware and bot domains will have a single return code range to differentiate the codes easily,” it is noted in the post.
 14 DAY TRIAL //
14 DAY TRIAL //