Spam botnets rely on all sorts of tricks to evade modern spam detection systems. One interesting botnet is StealRat, which relies on two hijacked websites and one compromised machine to send out spam.
According to experts from Trend Micro, the infected machine is used to connect the spam server to the website that's responsible for sending the spam.
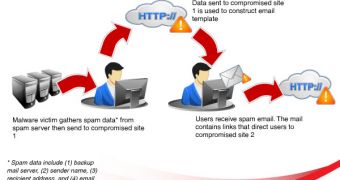
The malware victim gathers spam data such as backup mail server, sender name, recipient address and email template from the spam server. The information is forwarded to the compromised site, which is utilized to construct the email and send it out to users.
The emails sent out by the first compromised site contain links to the second compromised site that serves the payload (an adult website or a rogue pharmacy).
This way, since there’s no direct connection between the spam server and the spam, it will appear as if the email came from the infected machine.
“The spam mail itself does not spread the malware, so there is no visible link between the two as well. In essence, they have separated the core functions and minimized interactions among them to cut-off any threads that could link them to each other,” Trend Micro Threat Response Engineer Jessa De La Torre noted.
During the course of its investigation, Trend Micro identified 85,000 unique IP addresses and domains that were used to send out the spam emails over a one-month period. Each of these domains contain an average of two spamming scripts.
At least 8.640 spam data records are sent each day from the infected machine. As far as the recipients are concerned, the spammers are currently rotating around 7 million email addresses.
 14 DAY TRIAL //
14 DAY TRIAL //