Back in June, Kaspersky researchers revealed the existence of Backdoor.AndroidOS.Obad.a, a mobile threat which they claimed was the most sophisticated Android Trojan they had ever seen. After further analyzing the malware, experts have found that it’s being distributed with the aid of mobile botnets.
According to Kaspersky, Obad.a is the first mobile malware that’s distributed with the aid of botnets developed with a completely different mobile malware.
The mobile botnet used to deliver Obad.a is powered by SMS.AndroidOS.Opfake.a. The attack starts with a text message that attempts to lure recipients to a malicious website by telling them they’ve received an MMS message.
When the malicious site is visited, Opfake.a is automatically downloaded onto the user’s device as a file named “mms.apk.” If the app is installed, the command and control server can instruct the Trojan to send out a text message containing another malicious link to all the contacts from the infected device’s address book.
This second link points to a website that’s set up to serve Backdoor.AndroidOS.Obad.a as “mms.apk” or “mmska.apk.”
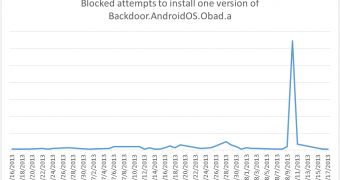
“In the space of five hours, 600 messages were sent with one of the Trojan- SMS.AndroidOS. Opfake.a modifications. In most cases delivery was via infected devices, while previously similar distributions used SMS gateways,” Kaspersky’s Roman Unuchek noted in a blog post.
“At the same time, only a few devices infected with Trojan-SMS.AndroidOS.Opfake.a distributed links to Backdoor.AndroidOS.Obad.a, so we could conclude that the creators of the dangerous Trojan rented part of a mobile botnet to spread their brainchild.”
The mobile botnet is not the only method used by cybercriminals to distribute Backdoor.AndroidOS.Obad.a.
Researchers say the individuals behind the sophisticated Trojan have also used traditional SMS spam and fake app stores that mimic Google Play. In addition, they’ve also leveraged hacked legitimate websites to redirect users to malicious domains.
So far, 12 versions of Obad.a have been identified, over 83% of them being aimed at users from Russia. Some samples have also been spotted in Kazakhstan, Uzbekistan, Belarus and Ukraine.
The Android vulnerability that allows the Trojan to gain DeviceAdministrator rights has been patched by Google but only in Android 4.3.
 14 DAY TRIAL //
14 DAY TRIAL //