A fresh exploit has been uncovered in smart TVs featuring support for the Hybrid Broadcast Broadband TV (HbbTV) standard that permits launching Internet content on the TV.
Yossef Oren and Angelos Keromytis at the Columbia University Network Security Lab discovered that the devices are susceptible to untraceable attacks that can last for as long as the TV is turned on.
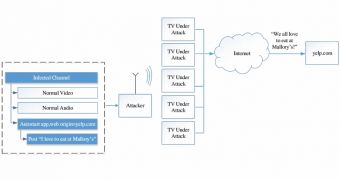
The attack has been dubbed “Red Button” because that’s what you need to press in order to access the online content; it can be used for distributed denial of service, un/authenticated request forgery, intranet requests, phishing and social engineering and exploit distribution.
The HbbTV specification allows broadcasting streams to include embedded HTML content and render it by the TV set. Because it is a pan-European initiative, the feature is not currently widespread in US, where adoption is at the beginning.
According to the two researchers' analysis of the specification, the broadcast and broadband systems are combined insecurely, enabling radio frequency (RF) injection exploitation from a localized device, which makes it close to impossible to detect.
This means that any gadget with RF equipment can be used to carry out the attack, such as a hovering drone outside the victim’s window.
What makes hybrid TVs vulnerable is the fact that when an HbbTV application embeds the web content into the broadcast data stream there is no defined origin because the “same-origin policy” does not apply, as is the case with content downloaded via a URL.
According to the report, “the HbbTV specification suggests that the broadcast stream should explicitly define its own web origin by setting the simple_application_boundary_descriptor property in the AIT to any desired domain user name.”
As such, an attacker can hijack the stream and inject malicious code that can take control over the TV and the devices connected to it, as well as steal personal information from accounts that are signed in on the TV.
Once an attacker gains control of the device, there is no sign of any background activity and the TV set continues to function normally, displaying the broadcast content.
In theory, detecting the attack is possible and can be done by using triangulation methods, which require receivers to be placed in the proximity of the attack and locate the rogue transmitter based on the receiver signal strengths.
However, given the effort and resources required to detect the perpetrator and taking into consideration that the attack is not long-termed, the wrongdoer would have plenty of time to make their escape.
 14 DAY TRIAL //
14 DAY TRIAL //