On November 10, the world found out that the FBI arrested six Estonians for allegedly running the largest, most sophisticated cybercriminal scheme the world has ever seen so far.
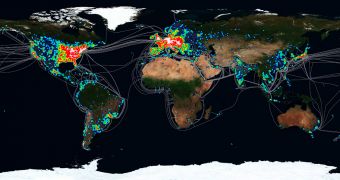
After two years of intense investigations conducted by the FBI in collaboration with Trend Micro, the operation was shut down, but the damages caused were enormous. The crooks managed to make $14 million (10 million EUR) by infecting 4 million computers, belonging to individuals and companies from more than 100 countries.
While the prosecution in this case is still continuing, Trend Micro's Advanced Threats Researcher and key liaison with the FBI, Paul Ferguson, was kind enough to answer a few questions related to how the security solutions company helped track down and annihilate the criminal network.
Softpedia: Before we start, please tell our readers a bit about yourself and your role with Trend Micro.
Paul Ferguson: Before coming to Trend Micro, I was an architect for Cisco Systems during the early- to -late 1990's -- I helped build massive networks all over the world.
When I left Cisco, network security became much more of a factor (that could no longer be ignored), so I started focusing on it full-time around 2000.
Softpedia: What was your part in the investigation that targeted this particular cybercriminal operation? Were you part of it from the start?
Paul Ferguson: I was one of the team members in my group that discovered, enumerated, and investigated the Rove Digital criminal enterprise beginning in 2006.
Softpedia: Technically speaking, what was Trend Micro's actual contribution?
Paul Ferguson: Members of my team *discovered* the criminal infrastructure, completely mapped out the size & scope, enumerated the methodology, as well as the criminal enterprise. We also were the catalyst in pushing U.S. Federal Law Enforcement to pursue indictments and successful prosecutions.
Softpedia: What were the means used to track down the gang? Are there any special tools you utilized, or did you rather rely on certain techniques?
Paul Ferguson: I cannot go into a lot of details here, for fear of disclosure of information that may jeopardize the ongoing prosecution of this case. Please refer to our published blog entry.
Softpedia: Trend Micro released a great advisory for individuals to check if their computers were unknowingly part of the scheme. Any other advice for the potential victims?
Paul Ferguson: Work with their ISP.
Softpedia: Do you believe that the techniques used to apprehend the suspects in this case can be utilized to shut down other similar malicious operations? Do you see Trend Micro expanding its efforts to bring more cybercriminals to justice in collaboration with law enforcement organizations?
Paul Ferguson: Yes. More so. It is a great example of how the public-private relationship can actually work. It doesn't always work, but occasionally it does.
 14 DAY TRIAL //
14 DAY TRIAL //