Popular websites are always a target for cybercriminals, and in a recent campaign, YouTube statistics tracker SocialBlade.com has been compromised to steer users to pages serving the Nuclear Pack exploit kit (EK).
The malicious download was detected by the system operators at Malwarebytes, who notified the administrator of the website to take the necessary measures for cleaning up the code.
SocialBlade is a tracking website for YouTube statistics that allows users to keep tabs of their progress on the video repository website, check potential estimated earnings or compare data with that of other YouTube users.
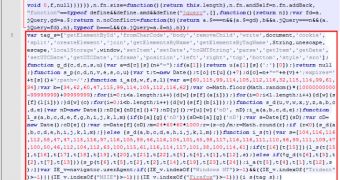
Jerome Segura from Malwarebytes analyzed the redirect procedure in order to determine how it originated. It turned out that the crooks did not inject an easy to find iFrame, but instead inserted the malicious code in a core JavaScript file.
Most of the times, the code cannot be identified easily and it is not necessarily flagged as bad. The server logs provided by the SocialBlade.com administrators showed that the compromise was the result of cross-site contamination and that the malicious code would be loaded into each file when the site was rendered.
The infection started from a neighboring blog that had not received updates in a long time, Jerome Segura told us.
Although it has not been confirmed, it is possible that the crooks leveraged the recent vulnerability affecting the MailPoet plugin for WordPress, revealed at the beginning of the month.
Sucuri, a company providing services for protecting website integrity, warned last week that they saw “a massive influx of broken WordPress websites,” which they quickly associated with the flawed MailPoet version, allowing the attackers to inject code in the pages of the affected websites.
If the affected website shared the same web server with other sites, cross-contamination could occur, extending the attack to other online resources.
Segura says that once the redirect to the page with the exploit kit is complete, exploits for vulnerabilities in Adobe Flash Player, Adobe Reader, Java and Internet Explorer are funneled into the users’ computers.
The payload contacts a remote location and then tries to download a file that “most likely leads to ad-fraud related malware (clickjacking etc.),” according to the researcher.
Malwarebytes has contacted SocialBlade.com and they acknowledged the website infection, pinpointing the exact source of compromise and eliminating it. At the moment, SocialBlade.com should be rid of any malicious code, as Malwarebytes systems no longer detect suspicious activity.
Statistics from SimilarWeb show that SocialBlade.com recorded a number of visits estimated to 3.6 million in June 2014.
 14 DAY TRIAL //
14 DAY TRIAL //