Security researchers have identified a couple of critical vulnerabilities in Skype. One of them allowed an attacker to reset the usernames and passwords of any Skype account, and the other one could have been leveraged to bypass session token protections.
The ones responsible for finding the security hole are Vulnerability Lab researchers Benjamin Kunz Mejri and Chokri Ben Achour who have once again demonstrated their impressive bug-finding skills.
In the past, they managed to find flaws not only in commercial products utilized by millions of users worldwide – including MSN, PayPal and Barracuda –, but also in applications or services used by government and military organizations.
One noteworthy fact is that the password reset vulnerability is different from the one found a few days ago on some Russian forum. These security holes were reported to Skype at the beginning of October and they were addressed by the company a few weeks later.
Initially, we believed that they were one and the same because Skype representatives failed to notify Vulnerability Lab that the issues they had reported were fixed.
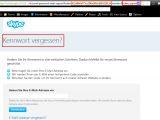
The experts found that a remote attacker could compromise any account by exploiting a flaw in the account recovery function available on the official Skype website. The most worrying part was that no user interaction was required to exploit the remote bug.
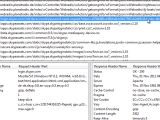
“In the recovery function there is an authentication request bound to the account session using the ‘json’ form with ‘jquery’ and the value of the ‘intercape.’ The request itself is not sanitized. The value is only checked if it exist or if it’s empty, but it does not validate the context again,” Benjamin Kunz Mejri, CEO of Vulnerability Lab, told Softpedia.
“The attacker can bypass the token protection via live session tamper to reset any account by exchanging the local values with his own. Exploitation requires `processing to request` via ‘jquery’ implement ‘JSon’ form request.”
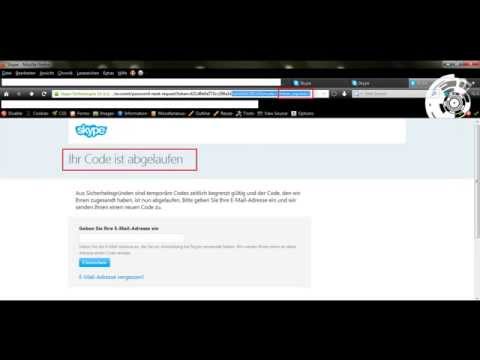
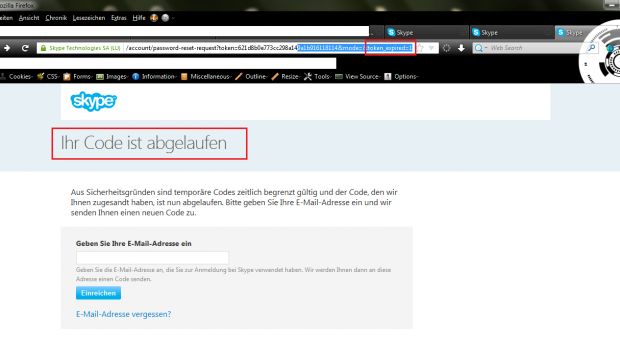
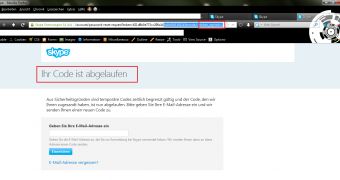
“It is only possible to manually exploit the remote vulnerability by using a session tamper tool like Tamper Data. A remote attacker can, for example, bypass the token protection with values like ‘*/+[New Account Details] or [New Account Details]+/*’ to reset random Skype application accounts or infiltrate specific accounts by changing usernames or passwords,” he added.“The high severity application vulnerability is located in the recovery account function of the Skype account service application. In the recovery notification mail function there is a GET request and a link which expires after 6 hours,” the researcher noted.
“The bug affects the reset function when processing to load the token_expire parameter with the 1 value (invalid). Attackers can change the stable URL by using a zero (0+ / +0) to bypass the checked token_expire value (parameter) and get a valid link with the expired session.”
Users who are passionate about the technical side of such research can check out the proof-of-concept made available by the experts here and here.
Video POCs have also been made available.
Session token_expire protection bypass:
Username/password reset vulnerability:
 14 DAY TRIAL //
14 DAY TRIAL //