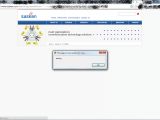
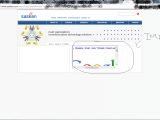
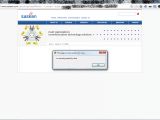
Independent security researcher Shadab Siddiqui sent us a number of screenshots to prove that one of India’s largest telecoms companies is having difficulties in securing its public website.
Sasken provides a large variety of services, including research and development consultancy, wireless software products, and network engineering services to organizations worldwide, but as it turns out, security is not their strongest point.
Siddiqui reports that their website doesn’t contain only the common cross-site scripting (XSS) vulnerabilities, but also others such as an XPath Injection issue that can be easily exploited.
“X-path injection is a type of web attack which targets a website that create XPath queries from user-supplied data. Querying XML is done with XPath, a type of simple descriptive statement that allows the XML query to locate a piece of information,” the expert said.
“By sending intentionally malformed information into the web site, an attacker can find out how the XML data is structured, or access data that he may not normally have access to.”
As the images provided by the researcher show, the website is poorly coded, which is something that one would not expect to find with a company that's appointed as being among the best places to work in India.
The XSS and SQL Injection security holes on the site are highly dangerous, giving ill-intended hackers the opportunity to cause serious damage, but XPath Injection involves even more risks.
“XPath Injections might be even more dangerous than SQL Injections since XPath lacks access control and allows querying of the complete database (XML document), whereas many SQL databases have meta tables that cannot be accessed by regular queries,” he explained.
The screenshots also demonstrate how a cybercriminal can alter the site to inject his own malicious content by relying on the Iframe Injection flaw.
We have contacted Sasken more than five days ago and informed them on the issues present in their website. So far we haven’t heard back from them, but the post will be updated as soon as more information becomes available.

 14 DAY TRIAL //
14 DAY TRIAL //