Simon Bell, the UK student that presented an in-depth analysis of the Simplocker code, has just released the solution for decrypting the files taken hostage by the ransomware.
It relies on using the built-in decrypt method and the password mentioned in the initial post.
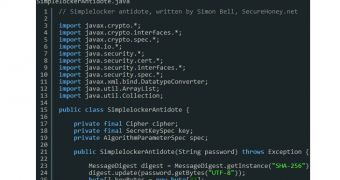
“This means we're able to create our own Java class and copy the decryption code from the ransomware into our antidote class,” writes Bell.
After creating a new Java class with the methods for targeting the encrypted data and for setting the decryption password, Bell integrated the constructor method in order to get the job done.
The compiled result should be able to look for the locked items and run the decryption routine on them. The student also provides an alternative for overriding the default cipher password.
The new post details all the steps necessary to build a Java application that can scan for the encrypted data and try to unlock it using the predefined password.
Getting to a successful result in this case was an easy job, but since Simplocker is considered more of a proof-of-concept than a real threat, future malware derived from it will feature code obfuscation and protection methods to prevent detection and analysis.
 14 DAY TRIAL //
14 DAY TRIAL //