The customers of 24 major financial institutions are currently being targeted by cybercriminals with the aid of the Caphaw Trojan, better known as Shylock. The malware is designed to steal banking credentials from the owners of infected devices.
Security researchers from Zscaler have been monitoring the attacks and found that the list of targeted banks includes Bank of Scotland, First Citizens Bank, Barclays Bank, Bank of America, Co-operative Bank, Chase, Comerica, Harris Bank, Regions, Intesa Sanpaolo, SunTrust, US Bancorp, and Wells Fargo.
Experts are not 100% certain how the malware is being distributed, but they suspect that the cybercriminals are using an exploit kit that leverages Java vulnerabilities to push the threat.
Once it’s installed on a computer, Shylock starts injecting itself into legitimate processes in an effort to avoid being detected by security solutions.
Another trick used by the cybercrooks to keep their operations alive involves the use of a domain generation algorithm (DGA) that allows them to generate a large number of quasi-random domain names.
These domains are utilized as command and control (C&C) servers from which the Trojan receives instructions. By using a DGA, the attackers make it more difficult for law enforcement agencies to disrupt the C&C infrastructure.
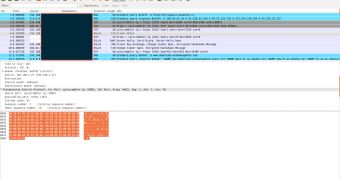
Shylock uses SSL encrypted traffic for communications between the infected hosts and various components of the C&C infrastructure.
As far as the malware itself is concerned, Shylock is developed in Microsoft Visual C++. It’s dropped on the targeted system in a folder and under a name that are quasi-randomly selected.
To make sure it’s persistent, the threat creates some registry entries.
Before stepping into play, Shylock checks to see if it’s running in a virtual machine environment and if an Internet connection is available. If a VM is detected or if there’s no Internet connection, the threat stops running.
Additional technical details on Shylock are available on Zscaler’s blog.
 14 DAY TRIAL //
14 DAY TRIAL //