Systems that have been immunized against Shellshock are still vulnerable to exploits for this vulnerability in Bash command interpreter, under certain conditions.
The attack would have to be carefully planned and multi-layered, but an experiment carried out by security researchers at Trend Micro shows that it can be done, unless preventative security solutions are in place.
A carefully-laid plan could help attackers get the job done
The overall plan is quite simple, and it involves substituting the patched version of Bash on the target machine with a vulnerable one; but implementation is not an easy task, as the attacker would have to acquire the appropriate access privileges into the network with the targeted system.
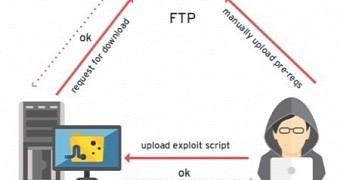
For demonstration purposes, the security researchers created a Python script to modify “/usr/sbin/service” so that it printed the text “vuln” when options of the service, such as status, start, stop and restart, were used. As per their scheme, a web server is necessary to run on the target.
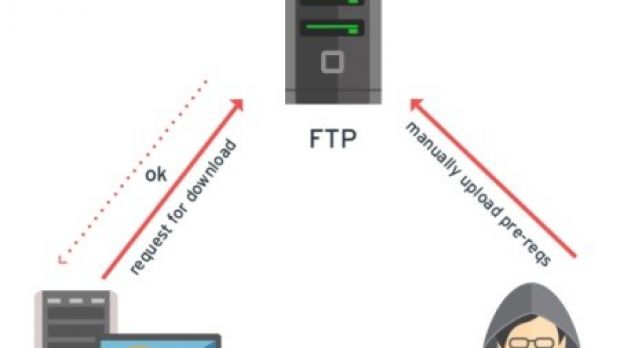
An FTP server would host the vulnerable version of Bash and the script, while a web service would expose an upload file REST method to the users and would also run it. This sort of setup is necessary for downloading and executing the script in order to initiate exploitation on the server side.
The web service is also necessary for uploading the Shellshock exploit to the web server. The exploit’s job is to download the buggy Bash package, decompress and set it up on the web server. It also downloads and executes the Python script.
If all this is set up, only a few steps are required to achieve the compromise of the system, and the most difficult part is uploading the Python script, which initiates the exploitation routine.
In-depth security strategy is required for sensitive systems
“Our experiment shows that under certain circumstances, patching is not a complete defense against Shellshock. An attacker with enough access to a system can still exploit Shellshock even on a patched system,” Trend Micro said in a blog post today.
Cybercriminals have already packed vulnerable versions of Bash and they could use them in future attacks. Moreover, the experts say that since builds of the command-line utility have different hashes, signature-based scanning would be of little help.
However, some mitigation solutions are provided and they consist in using Intrusion Detection/Prevention Systems (IDS/IPS) with deep packet inspection capabilities, which can stop a threat of this kind at network level.
These could be used in combination with application control policies to regulate which programs can run on a specific system.
“Patching in and of itself is no assurance that the Shellshock threat is no longer present; other solutions need to be in place to ensure that the threat is minimized. This highlights the importance of a defense in depth strategy: multiple steps and layers need to be in place to protect networks from various threats, even if they have been fixed,” Trend Micro says.
 14 DAY TRIAL //
14 DAY TRIAL //