The vulnerability in Bash command interpreter for Linux and Unix has been seen being exploited in the wild, only one day after it was publicly disclosed.
Patches are available, but the tool is included in most Linux operating systems powering web servers, and many administrators may not be as quick to perform the update to a safe version, which makes the machines vulnerable to attacks with different goals, such as stealing credentials or serving malware.
Successful exploitation could enable remote execution of code, allowing an attacker to gain control of the system. Proof-of-concept scripts are already available in the wild, since taking advantage of the flaw is a low-complexity task.
Website compromise attempts seen in the wild
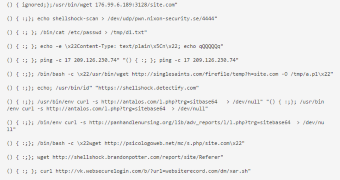
Daniel Cid from Sucuri, a company that offers services for keeping website integrity, says that immediately after the disclosure of the flaw (CVE-2014-6271), a small number of scans was performed, searching for vulnerable servers.
This type of activity is not unusual in such cases, as it is connected to researchers and administrators verifying their machines.
However, later on, Sucuri researchers started to see thousands of requests to various websites, trying to take advantage of the vulnerability. Attempts to set up remote shells and configuration of IRC bots were observed.
cPanel is a potential entry point, Cid says in a blog post, as some of the internal tools of the administration utility use Bash for executing CGI shell scripts.
“As we started to scan our clients’ sites (and the Internet as a whole) we found that about 2.9% of all sites we scanned were vulnerable to this problem,” he says. The percentage may seem small, but as Cid notes, “when we talk about millions of websites online, 2.9% is a lot.”
In a brief testing that did not include all the necessary variables that would render a more accurate (read “larger”) number of results, Robert Graham from Errata Security discovered about 3,000 vulnerable servers, when scanning on port 80 alone.
He also pointed to cPanel as a possible entry point, saying that “it's things like CGI scripts that are vulnerable, deep within a website (like CPanel's /cgi-sys/defaultwebpage.cgi).”
Tools for checking if websites are vulnerable to Shellshock have been set up online, including one from Sucuri, analyzing the web pages and returning the results in seconds.
Shellshock used to launch kernel exploit
Apparently, a sample of an exploit taking advantage of the Bash flaw has already been caught; it seems to be a kernel exploit with a command and control component, according to a GitHub post.
The message exchange between the malicious server and the client consists in sending the string “PING” and receiving the reply “PONG.”
However, Waylon Grange of Blue Coat, provider of security and networking solutions, says via email that in a different case his company has seen DDoS (distributed denial-of-service) botnets trying to use Shellshock and that traffic is expected to increase in the near future.
 14 DAY TRIAL //
14 DAY TRIAL //