A curious piece of malware has been identified by security experts from Seculert, Kaspersky and Websense. While there are some questions that remain unanswered, they've all noticed that the malicious element known as Shamoon covers its tracks by overwriting files and by wiping the computer’s master boot record (MBR).
Kaspersky experts believe that the creators of this Trojan are actually inspired by the “Wiper” found on the computers infected with the infamous Flame.
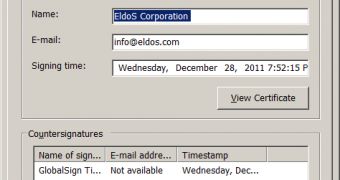
Another curious thing about Shamoon (Trojan.Win32.EraseMBR.a) is the fact that its disk driver is signed with a certificate from EIdoS Corporation, a security solutions provider.
Researchers from Seculert have found that Shamoon actually relies on a two-stage attack. In the first stage, the attacker takes control of an internal device that’s connected to the Internet. From this machine the infection is spread out to other computers that aren’t necessarily online.
After the computers are infected, the cybercriminals steal all the information they need and then they initialize the data wiping process.
Once this is done, the Trojan reports back to its command and control server through the machine it initially infected.
Unlike other malware, Shamoon doesn’t attempt to hide its presence for as long as possible. Instead, after it completes its tasks, it overwrites the files and deletes the MBR to ensure that no traces remain.
The main targets of the malware may be organizations from the energy sector. Websense has confirmed that at least one of the organizations from this sector has been hit by this threat.
It’s uncertain at this time who may be behind the malware, but according to Kaspersky, its name may be related to the Shamoon College of Engineering in Israel, or it might represent the name of the author (Shamoon is equivalent to Simon).
 14 DAY TRIAL //
14 DAY TRIAL //