Several websites belonging to security giant Symantec are vulnerable to cross-site scripting (XSS) attacks, according to a security enthusiast who discovered multiple flaws. The vulnerabilities could be leveraged to increase the credibility of email targeted attacks.
According to the XSSed project, who published mirrors of these proof-of-concept XSS attacks, the vulnerabilities were reported over the weekend by a researcher calling himself d3v1l. The bugs affect three distinct websites hosted under the symantec.com domain.
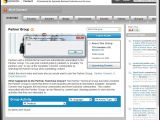
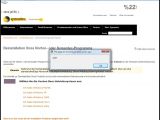
One of the flaws is located in a language selection field on symantec.com/connect/, a site dedicated to the company's community of business customers and partners. A second one is found in a feedback form loaded from seer.entsupport.symantec.com, a subdomain associated with the knowledge base for enterprise products. The third one is in the German section on the service1.symantec.com subdomain, which is part of international support site.
Cross-site scripting, also known as XSS, is one of the most common type of vulnerabilities on the Internet today. The bugs stem from a failure to properly sanitize input passed via forms, giving attackers the ability to pass content that gets interpreted as code.
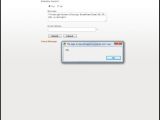
Fortunately, the vulnerabilities discovered by d3v1l are non-persistent in nature and can only be exploited by opening a malformed URL. However, these flaws can still be leveraged to enhance attacks, especially since they are located on the website of a trusted security vendor.
For example, an attacker could craft an URL that exploits one of these vulnerabilities to load third-party malicious code inside an iframe. He could make the rogue code serve a malware installer, then send emails masquerading as Symantec and advising users to visit the malformed URL and download the program. The fact that link is not spoofed and really points to a location on the symantec.com domain would significantly lower the vigilance of potential targets and increase the attack's success rate.
It is worth mentioning that a similar vulnerability was found on Symantec Connect over a year ago, which should have probably prompted a complete review of the website's code. In addition, at the beginning of last week, d3v1l also discovered an XSS bug in the language selector on updatecenter.norton.com, that has since been fixed.

 14 DAY TRIAL //
14 DAY TRIAL //