British security researcher Paul Moore has analyzed some online services of Santander to see just how secure they are. The research has focused on BillPay (santanderbillpayment.co.uk), the site that allows users to make online payments, and the mobile banking applications launched earlier this year.
Both BillPay, which is developed by a company called Headland, and the mobile banking apps are advertised as being secure. However, Moore warns that this is far from being true. He has uncovered several security issues that give cybercriminals numerous opportunities.
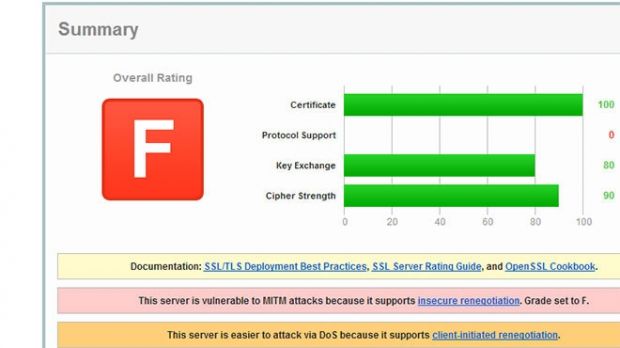
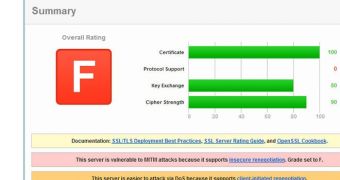
For instance, the BillPay website’s secure connection is not configured properly. The SSL testing application from Qualys gave it an F because the server on which the application is hosted supports insecure renegotiation.
“If a server is vulnerable to insecure renegotiation, it’s possible to carry out a MiTM or Man-In-The-Middle attack; allowing a hacker to inject arbitrary content into encrypted data,” Moore warns.
In addition, the SSL certificates are not installed correctly, which is demonstrated by the security warning that pops up when the website is visited from a mobile device.
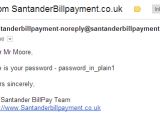
Besides the SSL issues, Santander BillPay is plagued by another serious problem. When users request a password reset, the bank sends them the password, via email, in clear text. This means that the passwords are stored without being encrypted.
The fact that users are asked to set strong passwords doesn’t do much good if the information is not stored securely.
Another vulnerability found by Moore on the website was a cross-site scripting issue that could have been leveraged by cybercriminals for phishing attacks.
As far as the mobile applications are concerned, both the personal and business versions are vulnerable to MITM attacks. Cybercriminals can easily intercept the data sent through the applications, including user IDs and passwords.
After numerous attempts, Moore was finally able to send a report of his findings to Santander. However, the financial institution has only managed to get the XSS vulnerability fixed.
The expert has told Softpedia that the password vulnerability still exists as of this morning.
The researcher highlights that these vulnerabilities have been found in around an hour without any automated tools being used.
“If Santander have missed the basics, what else have they missed?” Moore points out.
“If you can, avoid Santander like the plague. It’s poorly designed, insufficiently tested and vulnerable to a wide variety of exploits. If you come across a site connected with Headland in any way, tread very carefully,” he concluded.
For additional technical details, check out Moore’s Rambling Rant blog.
Update. Paul Moore says Santander have fixed all the flaws, except for the weak password storage issue. According to the expert, Headland needs to change the code and the database in order to address this problem.
 14 DAY TRIAL //
14 DAY TRIAL //