A new version of the Selfmite SMS worm for Android, reported in late June to rely on affiliate marketing to make money, has been found to rely on a different, more aggressive method to reach the same goal as the original variant.
SMS service has been maintained as the propagation method, and this time, the crooks chose a more attractive app to deliver the worm. According to security researchers, the malware can now inject code into the legitimate Google Plus app.
Once the threat is installed, it starts sending messages to all entries in the contact list, with links shortened through the GoDaddy service (x.co); the URL points to a malicious app.
When the list of contacts is exhausted, Selfmite.b restarts the message sending process, which could result in an increased phone bill for the victim. It seems that in no more than ten days, Selfmite sent 150,000 texts from more than 100 infected devices in 16 countries.
There are several changes available in this variant of the threat, which make it clear that the actors behind it have become more organized and are looking to get the most out of Selfmite.
Improved Selfmite downloads configuration file
When it was first spotted, Selfmite’s purpose was clear: propagate through the short message service to a limited number of individuals in the contact list and force a copy of Mobogenie on the victim’s device; this second action is crucial for the operators behind it to make money because they get paid for each installation of the application.
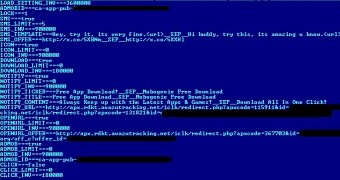
Researchers at AdaptiveMobile, who also discovered the first version of the worm, noticed that the crooks diversified the money-making scheme through a more complex set of instructions downloaded by the malware from a command and control server.
The configuration file instructs Selfmite to advertise the services the crooks get paid for according to the IP of the victim. As such, users in different geographic regions are delivered different content.
AdaptiveMobile says that two icons are created on the Android screen and “if user clicks on one of the icons the following content he receives depends on his country of origin.”
They noticed that a user from Ireland would be pointed to a premium subscription page, while one in Russia would receive the Mobogenie app, just like in the initial variant of the malware.
Selfmite takes advantage of more opportunities to make money
The configuration file is also used for a second monetization method, involving a compromised Google Plus app. Starting the app redirects to a different one in Google Play, probably also part of the pay-per-install scheme.
Upon closing it, a subscription offer for a certain service is automatically opened in the mobile web browser. AdaptiveMobile says that the subscription type is subject to change, depending on the configuration file.
By forcing unsolicited content on users, the operators ensure a revenue stream from advertising and referral networks.
The researchers say that, when a text message from an infected victim is accessed from an iOS device, the shortened URL redirects to the fitness app in Apple Store.
Because of the more aggressive approach used in the current Selfmite variant, the number of victims is much larger than in the case of the earlier version. “Plus it’s many ways of monetization together makes Selfmite.b a really serious issue,” said the researchers.
 14 DAY TRIAL //
14 DAY TRIAL //