Experts from security solutions firm Trusteer highlight the fact that social engineering plays a very important role in phishing attacks. They also reveal that shady notifications that purport to address security issues are the most successful.
Cybercriminals have noticed that people fear for the safety of their data and the integrity of their bank accounts. That’s precisely why their malicious messages are designed to rush the potential victim in taking a decision.
In many situations, they also make threats to ensure that the user takes them seriously.
Here’s an example of a phishing email which informs bank customers that their accounts have been locked: We locked your account because we needed to draw your attention to the fact that you didn’t complete our security online form for the year 2012. The form expires today and we need you to finish the process right away.
Accountholders may be concerned by the fact that they might not be able to access their funds and services, so they rush to complete the process and hand over the information requested by the crooks.
In another example, the scam artists tell victims that someone has been accessing their bank account:
This message has been sent to you from [name of bank] because we have noticed invalid login attempts to your account, due to this we are temporarily limiting and restricting your account access until we confirm your identity.
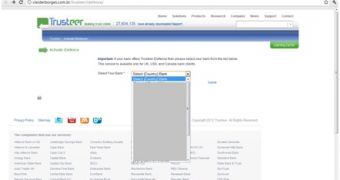
Just as successful are campaigns that leverage the names and reputations of security firms. Trusteer have found that a number of phishing sites and phony notifications rely on their name to promote so-called “security features.”
The malicious offer urges the recipient to click on an Activate Now button, which leads to a website that almost perfectly replicates the Trusteer site.
Here, users must chose the name of their financial institution from a dropdown list. Once the bank is selected, the unsuspecting internaut is taken to a site that resembles the one of the organization.
While these scams originate from various cybercriminal groups, bearing different subjects and leveraging diverse topics, they all have one thing in common. They ask for information - such as ATM PINs, passwords, credit card numbers, and CVVs - which a legitimate firm would never request from its customers.
Note. My Twitter account has been erroneously suspended. While this is sorted out, you can contact me via my author profile or follow me at @EduardKovacs1
 14 DAY TRIAL //
14 DAY TRIAL //