Online banking malware identified by Trend Micro as VAWTRAK has been discovered to abuse Software Restriction Policies in Windows in order to disable the activity of various security applications installed on the system.
According to Microsoft documentation, these policies can be used against viruses, to define the ActiveX controls that can be downloaded, execute digitally signed scripts only, enforce that only approved software is installed on the system and lockdown a machine.
What VAWTRAK does is look for folders belonging to security software and add a registry entry that forces all the files in the location to be executed with restricted privileges. The added registry entry is the following:
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\Safer\CodeIdentifiers\Paths\{generated GUID for the AV software} ItemData = “{AV software path}” SaferFlags = “0”
The directories targeted by the threat are under “%Program Files%” and “%All Users Profile%\Application” locations, used by numerous security utilities.
The list is quite large and the products affected belong to reputed vendors, among them being Avast!, Bitdefender, ESET, Emsisosft, Kaspersky, F-Secure, Malwarebytes, Symantec, Avira, Panda Security and even Trend Micro.
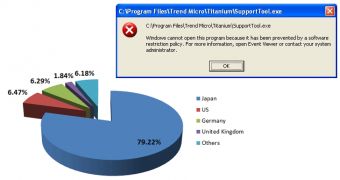
The effect of the privilege restriction is the impossibility of the files available in the targeted folders to run, the user being informed through an error message that the operating system could not open the program because it is under a software restriction policy.
“This is not the only time we have seen this tactic used, but the prominence of recent VAWTRAK attacks means there are more users affected by it than normal,” said Marilyn Melliang, Senior Threat Research Engineer at Trend Micro.
The VAWTRAK malware family included backdoor and information stealing features, but the results of a recent investigation of the threat carried out by Trend Micro revealed that it can now steal banking credentials from the infected systems as well.
In a company report, it is noted that Japan is the country most affected by VAWTRAK, with the United States very far behind, as “feedback from the Smart Protection Network indicates that the top countries affected by this threat are Japan (79.22%), United States (6.47%), and Germany (6.29%).”
Senior threat researcher Matsuka Bakuei said that, “the increase in banking malware targeting JP banks can be attributed to information stealing malware such as VAWTRAK and TSPY_AIBATOOK, that have added a functionality allowing it to steal banking credentials. Furthermore, traditional banking malware like ZeuS/Citadel is not the only malware which hit JP banks.”
National Police Agency informs (Jap) that an estimation of the losses due to unauthorized transactions in Japan reaches 1.417 billion yen ($13,9 million / 10,250 million EUR), recorded between 9 January and May, 2014.
 14 DAY TRIAL //
14 DAY TRIAL //