Security researchers have identified a vulnerability in the Android version of the digital music service Spotify that could allow attackers to run phishing campaigns against the user.
According to Trend Micro, the glitch is present in versions of the app earlier that 1.1.1, and if successfully exploited, it would permit taking control of what is displayed in the app’s interface.
Phishing is the most prevalent form of attack, and in this case, it may be used by cybercriminals to collect sensitive information such as passwords, email addresses, and even financial details, considering that Spotify also provides a paid service.
Simon Huang, mobile security engineer at Trend Micro, says that “the vulnerability affects a specific activity (com.spotify.mobile.android.ui.activity.TosTextActivity), which is designed to retrieve and show Spotify web pages on the app.”
As a result, the content of the web pages can be displayed in other apps available in the mobile device. The problem goes deeper than this, though, as there is the possibility for an activity to be initiated by a separate app, process, or thread without the need of additional permissions.
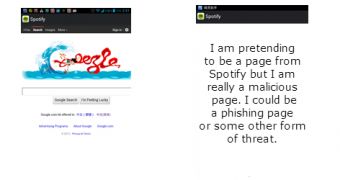
By exploiting the flaw, the security researcher was able to bring the Google home page in the interface of the Spotify app.
He warns that minimizing the activity can be done without restriction, and if the potential victim uses the “back” button to stop Spotify, the malicious content pops up on the screen.
Spotify responded to Trend Micro’s notification and released an update for the app. All users are advised to get the latest version, 1.1.2, as soon as possible in order to eliminate the security risk.
 14 DAY TRIAL //
14 DAY TRIAL //