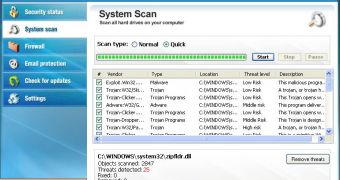
As a general rule, makers of fake antivirus software copy legitimate security solutions in order to give their own programs a feeling of authenticity. It’s a common occurrence for rogue antivirus programs to sport a look and feel similar to those of a genuine one, and especially to feature similar labels. Case in point: Security Essentials 2010, a fake antivirus program that attempts to pass itself for Microsoft Security Essentials. In the screenshot at the top of this article, users can see what Security Essentials 2010 looks like in order to know what to stay away from.
Most importantly, when Security Essentials 2010 or any other suspicious program, tries to bully users into paying for a license claiming that their system is crowded with malicious code, they need to understand that they are in fact infected with a fake antivirus program and not pay a single cent. The rogue antivirus, also known as scareware, attempts to trick the users into paying for a useless license, in order to remove inexistent threats that are falsely reported to have infected the machine.
“Well, it had to happen eventually. One of the oldest tricks used by rogue antivirus products is to use a similar name as, or have a similar look and feel to, legitimate security software. It’s been commonplace for them to mimic the Windows Security Center. So it was inevitable that the day would arrive when a rogue would masquerade as something similar to Microsoft Security Essentials. If anything, it surprises me a little that it’s taken so long. This one calls itself ‘Security Essentials 2010,’” Microsoft’s David Wood revealed.
Security Essentials 2010 is in fact Trojan:Win32/Fakeinit, a Trojan horse that infects Windows PCs, and, despite claims to the contrary, does not remove malware. “Fakeinit’s downloader not only installs the fake scanner component – it also monitors other running processes and attempts to terminate the ones it doesn’t like,” Wood added. “Aside from this, it lowers a number of security settings in the registry, and changes the desktop background to display a (…) rather alarming message. It also modifies the registry in an attempt to prevent this background from being changed again. Furthermore, it also downloads and installs a Win32/Alureon component, and another Layered Service Provider (LSP) component, also detected as Trojan:Win32/Fakeinit. This LSP monitors the TCP traffic sent by various Web browsers that the user might have installed, and blocks any traffic to certain domains.”
Users should know that Microsoft Security Essentials is available as a free download, and that Microsoft only requires end users to be running legitimate Windows, but not to pay for licenses.
Microsoft Security Essentials is available for download here.
 14 DAY TRIAL //
14 DAY TRIAL //