In December 2012, experts identified a cybercriminal campaign aimed at various Russian industries. Cyveillance has also analyzed the advanced persistent threat and the company has found that the campaign has been highly successful.
The experts wanted to determine the malware’s rate of success against Russian targets. First of all, they’ve confirmed that the cybercriminals behind the malware – dubbed Sanny based on the email address used by the attacker – are based in South Korea.
In order to analyze the campaign, researchers have investigated the bulletin board used by the attacker as a command and control (C&C) server.
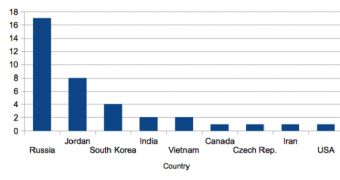
They have identified data originating from a set of 37 unique IP addresses, each representing a Sanny botnet node. Most of them have been associated with locations from Russia, but some have also been identified in Jordan, South Korea, India, Vietnam and Canada.
Cyveillance has determined that most of the IPs were with telecom companies that served as home broadband providers.
“In conclusion, the Sanny / Win32.Daws was highly successful in its targeting of Russia and especially Russophones. This is a growing trend in malware and in this particular case, it was within the capabilities of a smaller bad actor rather than a large malware gang or state organization,” experts concluded.
 14 DAY TRIAL //
14 DAY TRIAL //