The latest version of Internet Explorer fails to properly separate input from two different domains, allowing content belonging to one domain to be displayed in the context of another.
Web browsers feature a protection measure called same-origin policy (SOP), a set of rules ensuring that the origin of a piece of information (a document or a script) is preserved and does not interact with a resource from another origin.
Attack on major website demonstrates the flaw
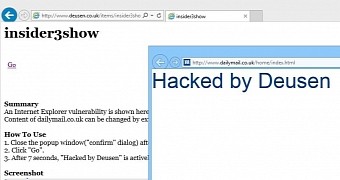
Security researcher David Leo found a way to bypass SOP in Internet Explorer and demonstrated the flaw by carrying out a cross-site scripting (XSS) attack on dailymail.co.uk.
Leo has created a proof-of-concept (PoC) that automates the attack, where arbitrary content is shown in the context of the DailyMail website. The address remains the same, but the content displayed is the one selected by the researcher.
The PoC is demonstrated by simply opening a page on the researcher’s website in Internet Explorer and accessing a link that triggers the vulnerability.
Next, the website of Daily Mail loads up in a separate frame and seven seconds later the arbitrary content pops up, preserving the original Daily Mail address.
Some pre-requisites are necessary for the attack to work, as Joey Fowler, senior security engineer at Tumblr, points out in a mailing list thread. If the targeted website does not contain X-Frame-Options headers with “deny” or “same-origin” values, then the attack will be successful.
He also adds that this method bypasses standard HTTP-to-HTTPS restrictions and that, while the payload is injected, “most Content Security Policies are also bypassed (by injecting HTML instead of JavaScript, that is).”
Victims are unaware of the trick
Leo carried out tests on Internet Explorer 11 running on Windows 7, but the SOP bypass also works on Windows 8.1, with the latest version of the web browser.
An attack of this type could be used by cybercriminals to steal sensitive information (credentials for online accounts) from the victim by serving them a rogue page that imitates the layout and design of a legitimate entity.
Using the same tactic, malicious files can be delivered without any hint to the user that the download originates from a different resource than the one of the trusted website.
The discovery is particularly important as multiple XSS attacks can be deployed. “It looks like, through this method, all viable XSS tactics are open,” Fowler said.
Mozilla Firefox and Google Chrome are not affected by this bug.
[UPDATE]: A Microsoft spokesperson contacted us via email with an official statement regarding the current SOP mishap:
"We are not aware of this vulnerability being actively exploited and are working on a security update. We continue to encourage customers to avoid opening links from untrusted sources and visiting untrusted sites, and to log out when leaving sites to help protect their information."
 14 DAY TRIAL //
14 DAY TRIAL //