A group of researchers from Europe and U.S. have successfully implemented a theoretical attack that subverts the security of the HTTPS protocol. The hackers generated a rogue Certification Authority (CA) certificate that was trusted by all major browsers and could be used to impersonate any secure website.
In a coordinated effort, security researchers from different organizations and institutes have demonstrated that virtually undetectable phishing attacks are possible, because some Certification Authorities still use the vulnerable MD5 hashing function. In fact, the research conducted by Alexander Sotirov, Marc Stevens, Jacob Appelbaum, Arjen Lenstra, David Molnar, Dag Arne Osvik, and Benne de Weger has the specific purpose of convincing Certification Authorities to drop MD5 and move on to more secure algorithms, such as SHA-1, SHA-2, or the upcoming SHA-3.
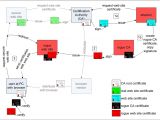
SSL (Secure Sockets Layer) is a cryptographic protocol aimed at providing network security by preventing data eavesdropping, tampering, or forgery. HTTPS, Hypertext Transfer Protocol Secure, combines the regular HTTP protocol with SSL, or the newer Transport Layer Security (TLS). “The vulnerability we expose is not in the SSL protocol or the web servers and browsers that implement it, but in the Public Key Infrastructure,” the researchers say.
The way HTTPS works is by browsers adding root CA certificates supplied by Certification Authorities to a trusted zone. Such a root certificate is then used to verify and validate any website certificate signed by the corresponding Certification Authority. In theory, this means that an attacker would need to hijack a legit Certification Authority in order to sign digital certificates that will be accepted by the browsers. However, in practice, older hashing algorithms, including MD5, are exposed to collision attacks.
A collision attack implies that two different data chunks can result in the same hash. The researchers instrumented a successful collision attack with the help of 200 Playstation 3 gaming consoles stacked together, thus creating their own rogue Certification Authority certificate. As explained, the consoles were chosen because the operations were “very suited for the special SPU cores of the Cell Processor that the Sony PlayStation 3 uses.“
This certificate allows them to sign website certificates for any website on the Internet, certificates that will be trusted by the browsers. This has huge implications on Web security, and poses significant dangers to the financial and banking websites in particular. The experts demonstrated their attack today, at the 25th edition of the Chaos Communication Congress in Berlin, by simulating a transparent man-in-the-middle attack. “If an unsuspecting user is a victim of a man-in-the-middle attack using such a certificate, they will be assured that the connection is secure through all common security indicators: a 'https://' url in the address bar, a closed padlock and messages such as 'This certificate is OK' if they choose to inspect the certificate.”
In addition, combining this method with a DNS cache poisoning, an attacker could redirect users to a fake website simulating a legit one, without any possibility for them to tell the difference and meeting all the security requirements. Furthermore, while this technique has been put into practice only for attacks over HTTPS, it has the potential of being used to develop attacks for other services that make use of certificates and MD5-based SSL, such as e-mail, instant messaging, Internet faxing, or VoIP.
A more in-depth explanation has been posted on the project's website and a demo page using the rogue certificate has also been set up. The fake certificate is also available for download, but in order to prevent any potential misuses it is set to expire after August 2004. Therefore, in order for the browser to properly validate it when visiting the demo site, the system clock needs to be set back to August 2004.

 14 DAY TRIAL //
14 DAY TRIAL //