Researchers from Vulnerability Lab have identified a couple of security holes in the framework of VOlk-Botnet 4.0. Private Edition, a malicious application whose origins have been traced back to Mexico.
VOlk-Botnet is a remote administration tool that’s often utilized in cybercriminal campaigns, its main goal being to modify hosts files (local pharming attacks). Identified by Kaspersky as Backdoor.Win32.VB.oyu, the threat was last seen in Latin America, where it was utilized against the customers of financial institutions.
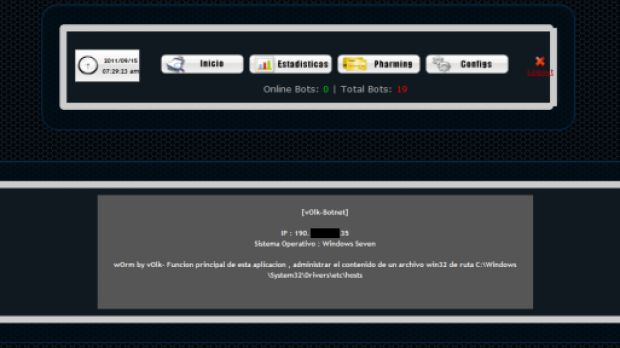
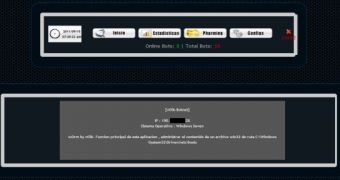
However, according to Vulnerability Lab experts, the malware’s developers haven’t done such a good job of properly securing their creation, leaving a number of holes that could be leveraged against the application’s control panel.
Apparently, a remote attacker could exploit the SQL Injection vulnerabilities that exist in the framework application’s Messenger, Filezilla and Estadisticas modules to inject his own SQL commands in the administrator panel and even take complete control of it.
Furthermore, such an attack against VOlk-Botnet doesn’t require any user interaction.
The Visit Webpage (Open URL), MSN Stealer, Download File and Setting modules have been found to contain input validation vulnerabilities which could be leveraged by a remote attacker to inject his own malicious script code, persistently, on the application side of VOlk-Botnet 4.0.
Attacks that exploit these flaws do require some level of user interaction, but if successful, the exploitation could lead to web context manipulation and combined CSRF manipulation. Furthermore, the method could be utilized to compromise the control panel via session hijacking.
Here is the interesting part. In the situations described above, the attacker is actually the victim, the user whose system is infected with the malicious element.
In the proof-of-concept made available by the researchers, they have revealed an interesting scenario in which an impacted users leverages the fact that the MSN Stealer module displays the bot’s name without sanitizing it.
“To infect the attacker back the victim can simulate a fake msn account login on a infected system with malicious persistent script code as Bot's Name. The result is a persistent script code execution out of Bot's Name web context in the messenger listing,” experts explained.
“The victim can hijack VOlk's Botnet Panel sessions or manipulate the framework with own malicious persistent context to stop, block, take over or disable the service.”
 14 DAY TRIAL //
14 DAY TRIAL //