In a newly detected smishing (SMS phishing) campaign, victims are incentivized to access a malicious link in order to cancel a potential fraud attempt.
Researchers at Trend Micro have discovered that a new mobile threat is currently spreading at a rapid pace in Taiwan as a result of a SMS phishing attack.
Cybercriminals send a short text message to the victim, informing them that they have applied to have the electricity bill paid online and providing them with a link where they can cancel the action. Victims are also offered to continue with the action via a different link, also malicious.
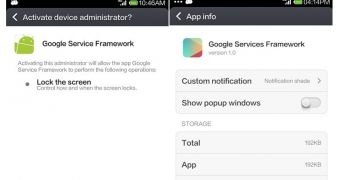
The link intended to cancel the action is malicious and takes the victim to a fake mobile app called Google Service Framework that can both send messages and intercept incoming ones.
Surprisingly, the app imitates a legitimate app from Google, by the name of Google Services Framework, and the differences between the two can go unnoticed by most users.
During installation, the fake app requests administrative privileges and runs as a service, making its removal more complicated.
The purpose of the malicious app is to profit from the micropayment services of the mobile carriers, which generally have to be confirmed by the user through an SMS.
The malware, detected as ANDROIDOS_RUSMS.A, can block messages from specific senders on the phone of the victim and direct them to the command server instead. Equipped with the capability to send and intercept messages, the threat can confirm the purchase on behalf of the user and thus complete the transaction without the victim finding out about it right away.
As a detection prevention technique, ANDROIDOS_RUSMS.A has virtual environment verification routines. If it detects that it runs in an Android emulator, all malicious behavior is suppressed.
Furthermore, the bad actors protect it with an APK packer that uses self-modification technology. “This means that the original code is encrypted and the unpacker code injected. When the app is launched, the unpacker code is run first. It then dynamically decrypts itself and recovers the original code in the memory,” says Yang Yang, a TrendLabs Mobile Threat Response Engineer.
He adds that the malicious links directing the victim to ANDROIDOS_RUSMS.A have been visited almost 32,000 times.
Reports about more elaborate and aggressive malware designed for mobile platforms have become more frequent.
Two examples are the Svpeng Trojan, which gained ransomware capabilities, and the first mobile encrypting malware, confirmed by both Kaspersky and ESET.
 14 DAY TRIAL //
14 DAY TRIAL //