Researchers from IT security firm Blue Coat have analyzed an interesting piece of ransomware most likely operated by Russian cybercriminals. This particular threat was delivered a couple of weeks ago in the attack on PHP.net.
According to Andrew Brandt, director of threat research at Blue Coat, the ransomware's functionality is pretty “standard.” It locks up the computer and threatens its owner for allegedly accessing illegal content. Victims are instructed to pay a so-called fine to have the device unlocked.
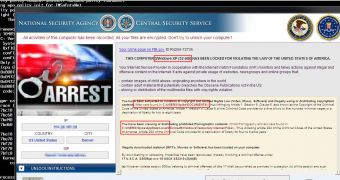
However, there are two noteworthy aspects about this piece of malware. One of them is the fact that it uses information from the victim’s user profile to deliver a customized lock screen. In addition, it leverages the name and reputation of the US National Security Agency (NSA) / Central Security Service to make everything more credible.
When it infects a computer, the ransomware checks for an Internet connection, after which it determines the targeted device’s location by using IP geolocation and online fraud detection service MaxMind.
Next, the threat sends some data to a server in Russia. Then, it uploads encrypted information to xaraworkbook.us, from which it gets the ransomware lock screen (see screenshot).
The lock screen includes the victim’s operating system, and even highlights the location on the hard drive where infringing content has been found.
On the other hand, while the username mentioned in the lock screen is correct, as it has been obtained from the victim’s user profile, the folder “C:\USERS” doesn’t exist in Windows XP.
Furthermore, the background of the lock screen, which appears to be a terminal, references Mac OS Kernel and BSD processes.
Unlike the CryptoLocker ransomware, which encrypts victims’ files, these types of threats can be easily cleaned up with an antivirus solution. That’s why you should never pay the amount of money the cybercrooks ask for.
 14 DAY TRIAL //
14 DAY TRIAL //