A malicious campaign active for more than a year, highly likely deployed for financial reasons, relies on sophisticated infection techniques to compromise computer systems belonging to financial departments of businesses in Russia and Ukraine.
The attackers use custom tools to check the information stored on the infected machine and resort to divertive tactics and legitimate code-signing certificates to avoid the detection of the intrusion.
Spyware is first installed on the compromised system
Dubbed Buhtrap by researchers at ESET, the campaign is believed to focus on accounting departments of different companies because the malware used includes references to software and banking applications employed by these divisions.
Furthermore, the researchers discovered that some of the command and control (C&C) servers used for communication with the threat resembled domains of accounting forums.
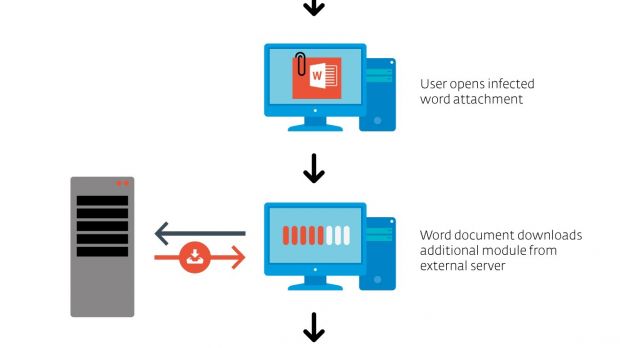
The compromise starts with an email claiming to deliver an invoice or a contract from MegaFon, an important mobile operator in Russia, under the form of a Microsoft Word document.
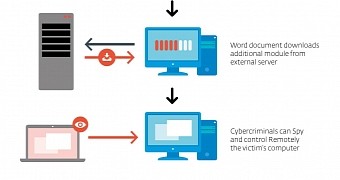
Once the computer is compromised, the hackers can control it remotely and record the activity of the user via keylogging and clipboard stealing modules.
The malware also features file download and execution functionality, allowing the intruder to add threats that could extend their grip on the machine or move to a different one in the network.
Benign software used to evade detection
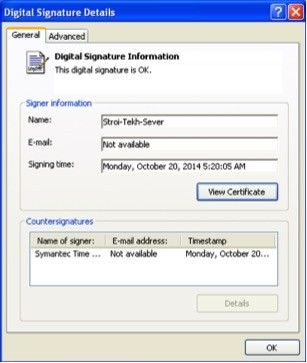
To evade detection, the hackers use one of four valid certificates to sign the malicious components. The certificates belong to companies in Moscow (Stroi-Tekh-Sever, Flash, OOO "Techcom" and Torg-Group).
Researchers believe that the certificates have been stolen and have already notified the issuer to have them revoked.
Apart from this, Buhtrap operators also resort to downloading benign software from the C&C server, along with malicious one.
“One of the benign archives we downloaded ultimately installed the Windows Live Toolbar. Although the means to install the software was malicious, the final payload wasn’t. These tactics were probably put in place to fool automatic processing systems: since a payload was downloaded, the system could be fooled into thinking that this is the end of the story,” ESET’s Jean-Ian Boutin says in a blog post.
Also contributing to detecting the campaign is the fact that multiple malware packages are used, and the modules they contained were not the same, suggesting that these are prepared depending on the target they are intended for.
Similarities with Carbanak found
According to data from the antivirus vendor, 88% of the victims are from Russia, and only 10% are from Ukraine. The remaining 2% is assigned to undisclosed regions.
Boutin says that all evidence indicates that Buhtrap is targeted in nature and operates in a similar manner as Anunak/Carbanak campaign, although there are differences that indicate a separate activity.
Despite using tools that have been seen before, Buhtrap is unlike traditional malware campaigns observed by the researchers, and it could set a precedent for other operations to adopt smarter tactics.
 14 DAY TRIAL //
14 DAY TRIAL //