Security researchers have analyzed the malicious GOM Player update file that was installed on a computer at the Monju fast-breeder reactor in Japan. The malware was detected after a worker installed an update for video playback software, namely GOM Player.
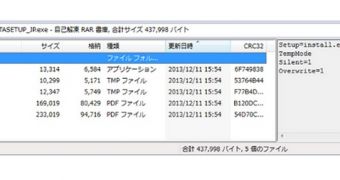
Kaspersky researchers say the nuclear plant employee responsible for the infection downloaded a file called GoMPLAYER_JPSETUP.EXE. This is actually a self-extracting RAR archive file that contains a legitimate update for GOM Player and another executable in RAR format (GOMPLAYERBETASETUP_JP.EXE).
This second archive contains five malicious files that unleash a backdoor detected by Kaspersky as Backdoor.Win32.Miancha.
The investigation is ongoing, so Japanese authorities haven’t provided too many details on the incident.
After news of it came to light, experts noted that this probably wasn’t an attack targeted at the nuclear facility, but a random infection caused by an employee’s carelessness. However, they’ve warned that nuclear plants, even defunct ones, should focus more on cybersecurity to prevent such incidents.
 14 DAY TRIAL //
14 DAY TRIAL //