A website of an undisclosed major company tied with software for simulation and system engineering has been compromised with rogue code for gathering intelligence about the visitors.
This could suggest that the threat actors plan a watering hole attack, given that the customers of the company are from sectors such as automotive, aerospace, and manufacturing.
The code on the website loaded a malicious JavaScript file, dubbed Scanbox by the attackers, from a remote server.
According to Jaime Blasco from Alien Vault, Scanbox’ behavior includes configuring the command and control (C&C) server where the information about the visitors is uploaded and collecting details about the referer, web browser used, geographical location, website content accessed, screen size values, operating systems and language.
Apart from this, the tool also collects data on the security software available on the system, along with products most often targeted by web-based exploits for installing malware.
Blasco also says that Scanbox implements keylogging functionality, recording all the keystrokes of the victim on the compromised website. This could be useful for learning the interests of the victim through search queries.
“While the user is browsing the compromised website, all keystrokes are being recorded and sent to the C&C periodically. It will also send keystrokes when the user submits web forms that can potentially include passwords and other sensitive data,” Blasco says in a blog post.
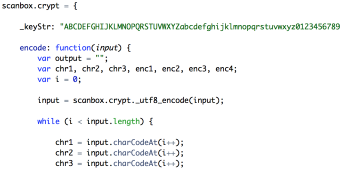
All the information uploaded to the C&C server is protected through encoding and encryption.
The company informs that Metasploit-produced exploits targeting different versions of Java have been observed in the same IP address that hosts Scanbox.
 14 DAY TRIAL //
14 DAY TRIAL //