Last week, we learned that Spanish police in collaboration with Europol arrested 11 individuals suspected of being involved in the development and the distribution of the notorious Reveton ransomware.
Despite the arrests, Internet users are still targeted with malicious emails designed to spread the threat.
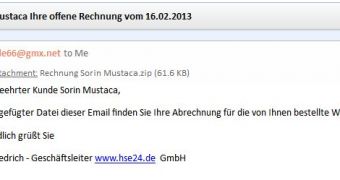
Avira experts have identified one particular email that’s highly clever. First of all, the notifications – which claim to carry an invoice from a popular German shopping portal – address recipients by their name.
The same technique is used for the name of the attachment, which looks something like “Invoice <first name> <last name>.zip.”
The archive file contains another .zip, which in turn hides an executable detected by Avira products as TR/Ransom.Foreign.acdb.1. The fact that it has been placed within two archives increases the chances for the threat to bypass security solutions.
“This method of packing the malware is very clever, because very few security solutions on gateways and most certainly no local solution, scans on more than one layer recursively inside archives. Using this technique the cybercriminals ensured that the payload goes through the security checks on its route to the user’s inbox,” Avira’s Sorin Mustaca explained in a blog post.
The expert has told Softpedia that Avira has been monitoring the Reveton ransomware, also known as the Police Virus or the BKA Trojan, but it’s still too soon to see if the arrests will have any positive effects.
According to Mustaca, despite the fact that the leaders of the cybercriminal ring have been arrested, it’s likely that they’ve already trained others to continue the operation.
He believes that we’ll see the first results after a week or so.
In a white paper released back in November, Symantec revealed that ransomware gangs could make over $5 million (3.9 million EUR) per year by extorting unsuspecting internauts.
 14 DAY TRIAL //
14 DAY TRIAL //