A new list of targeted financial institutions has been spotted in the configuration file of Retefe malware, which now aims at banks in Japan, too.
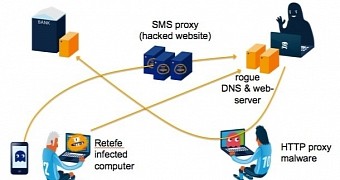
The Trojan is designed for man-in-the-middle (MiTM) attacks consisting of intercepting the connection from the user to the bank by changing the DNS (domain name server) settings, allowing to rout the connection through the cybercriminal’s infrastructure.
This allows full access to the traffic without raising the suspicion of the victim, who sees no sign of fraudulent activity.
Trojan is distributed through spam campaigns
Several botnets are used for generating spam messages and delivering them to different recipients. It appears that the new variant of Retefe comes from a compromised website that is promoted through spam messages, according to Peter Kruse from CSIS.
The researcher said that the malware was no longer available for download, but it would not be surprising at all to see the compromised domain used for other malicious campaigns.
Social engineering is again the weapon wielded by the attackers, who trick the victims into downloading and running the malware piece on their systems.
The routine followed by the threat after infection is simple: installation of a fake SSL certificate, changing the DNS server settings, and executing a self-delete command.
All this removes suspicion of malicious activity on the computer, since there is no threat to detect and the digital certificate shows the victim they’re communicating securely when connecting to the bank, when in fact the traffic is passed through rogue servers.
At least nine Japanese banks are targeted
However, the malware piece was caught in time by the researchers and analyzed. They found that the set of targets was modified and included more than 30 web pages belonging to several banks from Japan.
Among the examples provided are Chiba Bank, Yamagata Bank, Chugoku Bank, Japan Post Bank, Awa Bank, Daishi Bank, Hokkoku Bank, Musashino Bank, and Miyazaki Bank.
The malware is not new and it received attention from both security researchers and the media in the past, as it was employed in what Trend Micro dubbed Operation Emmental.
At that time, the threat actors sought to infiltrate on the computers of bank customers in Switzerland, Sweden, Austria and several other European countries.
Since in many cases two-factor authentication is enabled, the cybercriminals also direct the victim to download a fake banking application for mobile in order to intercept any codes sent by the bank to authenticate the user.
 14 DAY TRIAL //
14 DAY TRIAL //