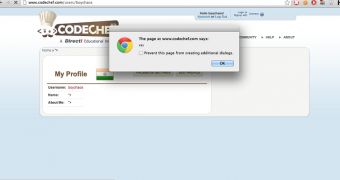
Security researchers Anshul Rohira and Shadab Siddiqui have identified a persistent (stored) cross-site scripting (XSS) vulnerability on CodeChef.com, the popular non-commercial programming community.
The experts highlight the fact that unlike reflected XSS security holes, persistent ones are far more problematic because they could be used not only to hijack user sessions, but also to permanently alter a website.
“Stored XSS is even more dangerous since the script is stored on the server and is executed everytime user visits an infected page,” Shadab Siddiqui told Softpedia in an email.
Fortunately, CodeChef provides security researchers with a special email address ([email protected]) where such issues can be reported. Hours after the experts submitted their findings, the website’s owners managed to patch up the security hole to make sure that their customers were protected against cybercriminal attacks.
On the other hand, the company didn't take the time to at least thank the experts for pointing out the existence of the flaws.
Email addresses such as [email protected] are useful not only for security researchers who practice responsible disclosure, but also for webmasters since they can benefit from pentesting that’s in most cases free of charge.
However, although in many cases they don't expect anything in return, those who are helped out should at least show some appreciation and properly thank researchers for their services.
 14 DAY TRIAL //
14 DAY TRIAL //