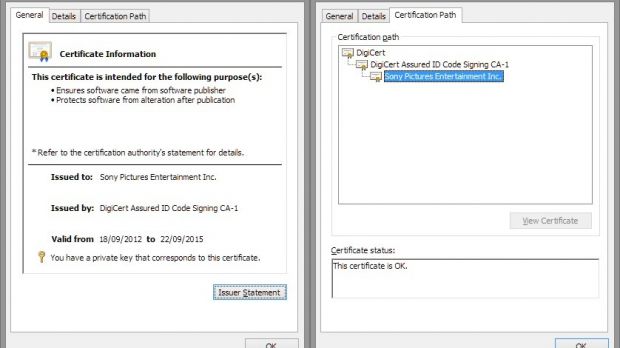
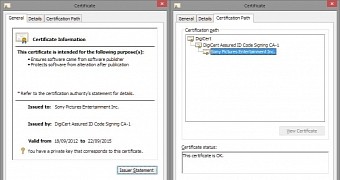
A sample of the malware used in the Sony incident in November was signed by a security researcher using a valid digital certificate from the data leaked online by Guardians of Peace (GoP), the hackers claiming the attack.
Then, the researcher uploaded the signed malware to online file scanning service Virus Total and reported the certificate to DigiCert, the CA (Certificate Authority) that issued it.
However, sending the sample to Virus Total drew the attention of security companies, Kaspersky in particular. The firm determined that the malware sample signed on December 5 was the same as another they had already studied.
Weak passwords are never a good idea
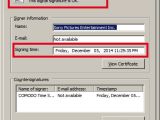
Independent security researcher Colin Keigher revealed on Twitter that another researcher, whose name remains anonymous, found the certificate in the cache of data released by GoP and tried to unlock it using the name of the file as the password.
The trick worked and he tested the certificate on a sample of the malware (called Destover by Kaspersky) used in the Sony incident, thus finding that almost two weeks after Sony got hacked, the company still did not initiate the revocation procedures. It is important to note that many other certificates were included in the GoP-released files.
GoP reportedly stole 100 terabytes of data
Revoking the leaked certificates should have been one of the first steps Sony should have taken in the wake of the incident, regardless of the fact that they were password-protected (brute-force attacks can be quite efficient).
Lack of proper action from the company could mean that it does not know what information the hackers stole from its computers.
Media reports say that GoP managed to exfiltrate about 100 terabytes of information from Sony. The data includes sensitive information about employees and collaborators, as well as projects of the company.
Moreover, the large amount of files stolen from the company computers suggests that the operation developed over the course of months so that traffic would not draw attention if the attackers worked from afar.
If this is the case, then making an inventory of what was stored on the computers and what could have been taken should be a pretty tall order. But even so, revoking the certificates could have been done simply based on the data leaked by the hackers.
Certificate has been revoked, not thanks to Sony
Since so many individuals managed to download it, so could Sony, especially since they knew that the password protection, as feeble as it was, would have bought them some time to complete the task.
The certificate used for signing the Destover sample made it on the certificate revocation list (CRL) on December 7, two days after its upload to Virus Total.
According to Kaspersky, dozens of PFX files, which contain the private key and the certificate, have reached public domain.
In an update on Wednesday to the initial post, Kaspersky said that the signed sample was not found in the wild and that their findings were published specifically because the presence of the digitally signed Destover meant that the certificate was no longer under strict administration.
 14 DAY TRIAL //
14 DAY TRIAL //