A recently discovered malicious tool establishes a remote desktop connection with the victim’s computer during an online banking session allowing the attacker to carry out transactions without raising suspicion of the fraudulent activity.
Dubbed KL-Remote, the toolkit is currently for sale on Brazilian cybercrime forums and it is designed to mask the thieving actions by creating an overlay with a fake message on the bank’s website, security researchers found in their analysis.
Attacker peeks into the victim's screen
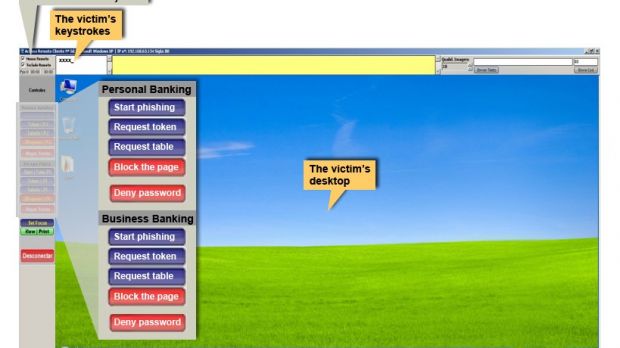
Carrying out the fraud requires manual intervention from the cybercriminal, who can initiate commands for displaying different types of communication on the screen of the infected machine, purporting to be from the bank.
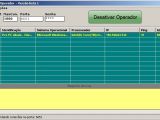
Itsik Avigdol, security researcher at IBM’s security division, Trusteer, has dissected the malware and the attack it has been designed for and learned that the control panel of KL-Remote alerts its administrator when the victim accesses the website of a targeted bank.
Once the remote desktop connection has been established, the attacker “is virtually looking over the victim’s shoulder, watching his or her every move,” said Trusteer senior product marketing manager Ori Bach in a blog post on Tuesday.
Triggering the alert for launching a banking website for the right targets is done based on a list of pre-defined URLs.
The initial information received by the cybercriminal includes the operating system of the compromised system, its IP address, CPU type and quality of the connection. These are probably useful in a later stage of an attack in order to select fitting graphics.
With a direct view at the infected computer’s screen, the attacker can check the activity and intervene at any moment.
Victim gets locked out, crook takes control of mouse and keyboard
According to the researchers, KL-Remote takes a picture of the legitimate website the victim navigated to and overlays it on the screen, preventing any interaction with the website.
The control panel of the malware features options to initiate phishing, as well as to ask for the two-factor authentication (2FA) token.
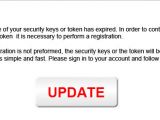
The phishing stage consists in presenting a message claiming to be from the bank, informing that the security keys for accessing the online banking service have expired and logging in once more is required. The 2FA code is the next piece of information requested.
“The tool contains separate messages for each of the targeted banks. Each message is customized to the bank’s website login/authentication process and copies its look and feel,” Bach says.
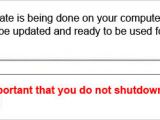
In the next step, the cybercriminals buy time to perform the fraud by overlaying a message showing that the security keys update is in progress.
At this moment, the victim is completely locked out and can do nothing but wait for the operation to complete, while the cybercriminal takes control of the mouse and keyboard and starts pilfering the bank account, all activity being masked by the fake message.

 14 DAY TRIAL //
14 DAY TRIAL //