The Red October espionage operation has been re-deployed, researchers believe, with a new malware toolkit that aims at the same victim profiles as before, relying on previously used themes for spear-phishing the victims.
The new threat uses Microsoft Office exploits, abuses cloud service provider CloudMe, and most of its targets are from Russia and Kazakhstan, with 15 and 14 infected systems, respectively, having been detected.
Red October hibernated for a while
Security researchers from Kaspersky started an analysis of a sample in August 2014 and noticed similarities to the tools and behavior of the malware kit used in the Red October campaign. The new threat was called Cloud Atlas.
Red October was uncovered in 2012 and Kaspersky spent several months analyzing the characteristics of the advanced persistent threat (APT).
At that time, they found that the campaign had been active for at least five years, focusing on exfiltrating sensitive and geopolitical information from diplomatic and government agencies around the world.
Most of the infections were recorded in Russia and Kazakhstan, but compromised machines were also detected in Azerbaijan, Belgium, Armenia, Iran, India, Ukraine, the US, Switzerland, or the UK.
Researchers say that immediately after publishing information about Red October, the campaign was shut down; however, they were expecting a comeback.
Strange exploit behavior
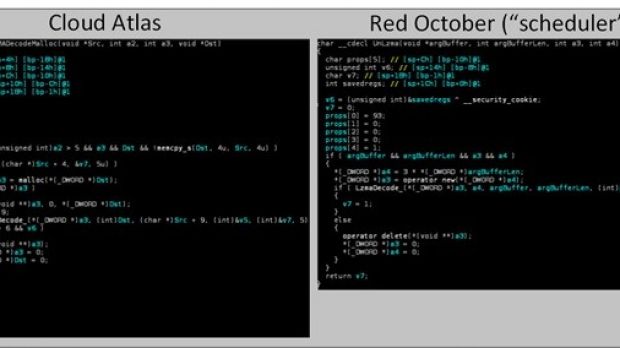
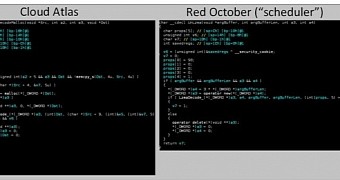
Cloud Atlas uses a variation of an exploit for Microsoft Office (CVE-2012-0158) which was also used in Red October, delivered via spear-phishing (maliciously crafted “Diplomatic Car for Sale.doc”).
The exploit does not write the backdoor on the disk directly. Instead, it places an encrypted Visual Basic script that drops a polymorphic loader and an encrypted payload, which has a different name every time.
In the process, a Run registry key is also added, in order to achieve persistence on the affected system; this way, the malware is launched at each computer start.
CloudMe used to store malware plug-ins and info from compromised PCs
The researchers from Kaspersky observed that the configuration file containing the details for the command and control (C&C) server is encrypted.
Upon processing the file, a link to a WebDAV server was found, which was used as a repository for various components of the malware and for the information exfiltrated from the victim’s computer.
The server, administered by cloud services provider CloudMe, is simply a piece of the infrastructure managed by the threat actor for C&C purposes. The company is not connected to the campaign in any way, the security firm stresses in a blog post: “the attackers simply create free accounts on this provider and abuse them for command-and-control.”
Multiple accounts have been created, and in one of them, the researchers discovered documents uploaded by the malware with details about the affected system, currently running processes, and the computer username. Everything is compressed with LZMA and encrypted using the AES algorithm (the keys were available in the malware body).
As per information from Kaspersky, other countries where Cloud Atlas was detected include Belarus (4), India (2), and the Czech Republic (2).
It is believed that the Red October malware has been written by Russian speakers and the exploits it relied on for compromising computers have been created by Chinese hackers.
 14 DAY TRIAL //
14 DAY TRIAL //