Other security flaws in Flash Player, patched by Adobe about a week ago, may have been integrated in Angler exploit kit (EK).
Earlier this week, French vulnerability researcher Kafeine announced that an exploit for the Flash Player vulnerability CVE-2014-0569 had been integrated in Fiesta EK.
This is a quick step for cybercriminals, since the details of the glitch had been reported privately to Adobe through the Zero-Day Initiative group and were not exposed to the public.
It is unclear how the exploit was created
With no proof-of-concept being released, it generally passes more time until an exploit for the vulnerability is created, but as Jerome Segura of Malwarebytes says, as soon as the fix is out, “skilled reverse engineers will start looking at the patch to be able to reconstruct the exploit.”
It is not known how the cybercriminals managed to obtain the necessary details; one theory is that they received a heads-up, another is that they have an extraordinary reverse engineer, the researcher added.
The sooner an exploit is created, the larger the number of users that have not applied the update. This obviously ensures a higher rate of success for the bad actors in their endeavors to compromise computers.
“That means we have less and less time to deploy and test security patches. Perhaps this is not too much of a deal for individuals, but it can be more difficult for businesses which need to roll out patches on dozens of machines, hoping doing so will not cause malfunctions in existing applications,” Segura said.
Bedep fileless malware also included in the malicious stream
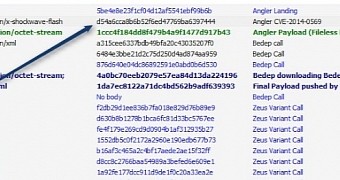
Although there is no certainty at the moment, Kafeine suspects that the new Angler EK includes an exploit for a different weakness that has been addressed by Adobe with last week’s Flash Player update.
The payload delivered to the affected computer is a variant of Zeus, which at the beginning had a low detection rate on VirusTotal; more recent scans show an improvement.
However, Kafeine has also detected that Bedep, a piece of malware that resides in the memory of the system and is not saved to disk, is also added to the compromised computer.
Initially, Kafeine believed that CVE-2014-0569 extended to other malicious tools; now he waits for input from other sources to determine which vulnerability is leveraged.
Regardless of the glitch the crooks try to profit from, one thing is certain: users need to update Flash to its latest version in order to reduce security risks.
“Browsing the net on an unpatched computer is like playing Russian roulette with a handful of loaded guns,” Segura said via email.
For cybercriminals, patched software translates to fewer infections, which is a heavy blow for their business.
CVE-2014-0569 "7day" is in Angler EK. Traffic redirected to Angler is massive. Update Flash ! http://t.co/ze627JYDWk pic.twitter.com/VEMCCYizfr
— kafeine (@kafeine) October 21, 2014
 14 DAY TRIAL //
14 DAY TRIAL //