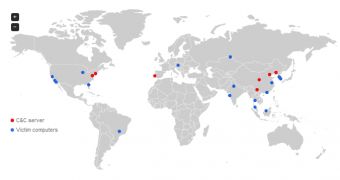
Security firm Trend Micro has released a real-time global botnet map which shows the locations of command and control (C&C) servers and the victimized computers they’re communicating with.
Botnets, the global networks of compromised computers that help cybercriminals achieve their malicious goals, have become highly problematic these days. That’s why security solutions providers are constantly monitoring them to have a better chance at mitigating the threats they pose.
According to the figures provided by Trend Micro's Smart Protection Network threat intelligence service, a total of 618 C&C servers have been active over the last 14 days.
During this period, these servers were communicating with over 480,000 infected computers.
By knowing exactly where command and control servers are located, Trend Micro can block them. This ensures that their customers can’t be served malware, or malware can’t upload information stolen from their computers to the C&C servers.
Check out the Global Botnet Map on Trend Micro’s website.
 14 DAY TRIAL //
14 DAY TRIAL //