The Federal Bureau of Investigation issued an alert for computer users to stay vigilant of ransomware scams, as their number has increased lately, naming CryptoWall as one of the latest threats.
Experts in the security industry have long warned about this trend, based on analysis of data collected by their systems from across the globe.
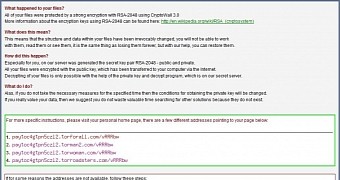
CryptoWall is already at version 3.0
Locking the computer on account of some bogus charges is one way cybercriminals try to get money from their victims, but a more damaging method that grew very popular among criminals is to deliver data encryption malware, such as CryptoWall, that unlocks the files when the fee is paid, with a secret key from the attacker.
The payment is done in bitcoins, a digital currency that does not rely on a central authority, and which does not require the owner to provide personally identifying information.
“A fairly new ransomware variant has been making the rounds lately. Called CryptoWall (and CryptoWall 2.0, its newer version), this virus encrypts files on a computer’s hard drive and any external or shared drives to which the computer has access,” the advisory from the FBI reads.
After locking the data, the victim is presented with the monetary demands, which can range from $200 (€173) to $5,000 (€4,300). Generally, if the victim does not pay within an initially specified timeframe, the fee doubles up.
Recently, version 3.0 of CryptoWall, also known as Crowti, has been spotted in the wild, featuring localized ransom messages and trying to connect to decryption services hidden in the I2P (Invisible Internet Project) network, which functions in a similar way as TOR anonymity network.
Malware spreads through shady emails and drive-by downloads
The FBI alerts that this form of ransomware is indiscriminate as far as its targets are concerned, as it has also affected government agencies, financial institutions, businesses or educational organizations.
The general recommendation is to create a backup copy with all important files and store it in a location not connected to the source computer.
Ransomware is not limited to computers, the law enforcement agency warns, as it has also spread to mobile phones; the same basic principle applies: devices are locked and the owner has to pay a fee to be able to use them again.
As far as distribution of this type of malware is concerned, it can be an email with a malicious attachment or pointing to a dodgy location that delivers the threat. However, the FBI says that drive-by download attacks have become more common, which generally exploit outdated web browser plug-ins and install the threat.
Keeping software installed on the computer up-to-date, especially the antivirus product, combined with maintaining regular back-ups of important data should help prevent infection with data-encrypting ransomware, as well as recover the files without having to pay the ransom.
 14 DAY TRIAL //
14 DAY TRIAL //