Security expert Brian Krebs has identified a ransomware cashout service that abuses a feature integrated into a US-based betting website to allow cybercriminals to launder their illegally earned funds.
Cybercriminals can make millions of dollars each year with the aid of ransomware, the malicious elements that lock up computers and keep them that way until the victim pays a ransom via services such as MoneyPak, PaySafe or Ukash.
While infecting computers with ransomware is not that difficult, converting the funds into cash is. In the case of MoneyPak, the crooks can spend the money they make at stores that accept it. They can also connect MoneyPak to a bank account, PayPal or prepaid MasterCard or Visa cards.
However, as Brian Krebs highlights, when you have a lot of MoneyPak codes collected each day, it’s not easy to cash out the money by using these methods.
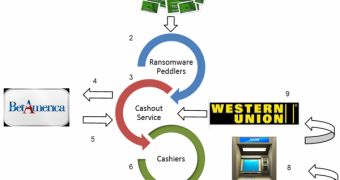
This is where a ransomware cashout service based in Minsk, Belarus, steps in. It abuses a feature in betamerica.com – a website that enables users to bet on dog and horse races in the US – which allows customers to fund their betting accounts by using MoneyPak codes.
In theory, the crooks can transfer their MoneyPak to Betamerica, from where they can withdraw the money.
Betamerica representatives have told Krebs that they’re aware of the account that’s been used for fraudulent activities and they’ve already blocked it. The company says it’s aware of attempts to launder money by using the MoneyPak feature from their website.
The Minsk-based service might try to help crooks launder their proceeds, but it’s not cheap. Customers are charged with over half of the value of submitted MoneyPak codes.
Krebs has determined that four different sets of actors participate in this particular ransomware operation: victims who agree to pay the so-called fine, the crooks that distribute the ransomware and obtain the MoneyPak codes, the cashout service, and the “cashiers” who take the MoneyPak codes submitted to the cashing service and withdraw the funds.
 14 DAY TRIAL //
14 DAY TRIAL //