Researchers from Trusteer, the IT security firm recently acquired by IBM, have come across a new variant of the notorious Ramnit malware. This new configuration of the threat is being utilized to steal sensitive data from Steam users.
According to experts, Ramnit uses HTML injection to achieve its goals. The malware is capable not only of bypassing the site’s password encryption, but also of making sure the attack is not detected by the targeted server.
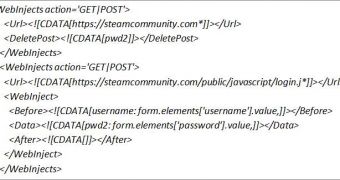
In the first stage of the attack, Ramnit injects a request for the password when users access the Steam login page and enter their credentials. This request allows the threat to bypass client-side encryption and obtain the password in clear text.
The problem with this technique is that the password is recorded in a new element labeled “pwd2.” Since the Steam server is not expecting to receive this element when the form is submitted, it’s likely that an alarm will be triggered and the malicious attempt will be detected.
In order to prevent this, Ramnit is designed to remove the injected element right before the form is sent to the website.
Researchers say there’s a perfectly reasonable explanation as to why the malware injects the element and then removes it.
“The answer is simple: by using form grabbing, the cybercriminal can easily index the collected data. When a key-logger is used, there is no indication of which characters are the username, which are the password and which ones are just irrelevant keystrokes – instead someone needs to manually separate the wheat from the chaff,” Trusteer’s Etay Maor noted.
In most attacks against Steam customers, cybercriminal rely on phishing and information stealing malware. However, this sophisticated Ramnit variant shows that they’re always preparing new techniques to be one step ahead.
 14 DAY TRIAL //
14 DAY TRIAL //