A variant of Remote Control System (RCS) spyware collected a month ago goes completely under the radar of some antivirus products, a security researcher reports.
RCS is a versatile product developed by Italian company Hacking Team that can work on different computer platforms, desktop or mobile, and it is developed specifically for government agencies for surveillance purposes.
Running malicious process not identified
The sample detection experiment was carried out by Claudio Guarnieri, the leading developer of Detekt, a free scanner specifically created to help journalists, activists and human rights defenders find on their computer systems traces of spyware known to be used by various government organizations.
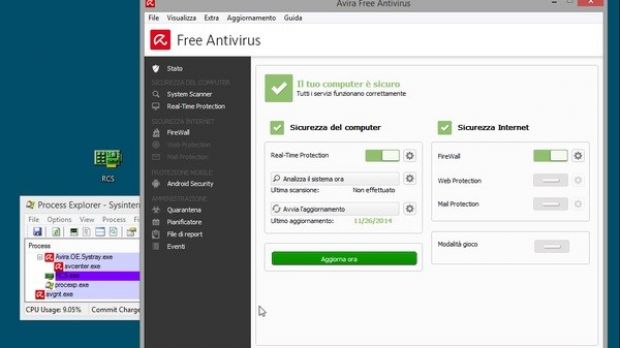
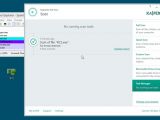
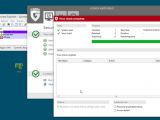
On Wednesday, he tested antivirus solutions from Kaspersky, Avira (Free), G Data and ESET and found that none of them were able to detect a trace of compromise on a system with an active RCS process.
There is no information about the configuration of the security products, but they were most likely running with the default settings. Even so, one would have expected the malware to have been picked up through one layer of defense, especially since its process was running on the computer.
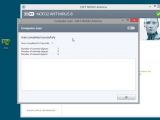
The researcher also showed VirusTotal analysis results from September 26 for the same sample, which revealed that at the time none of the antivirus engines could determine the malicious nature of the uploaded file. Antivirus companies listed on VirusTotal have access to the uploaded files.
Newer variants are also largely undetected
VirusTotal includes limited functionality of the antivirus solutions, so not all the detection features are used. Many products rely on behavioral analysis to detect malware that has not been previously classified.
Bogdan Botezatu, senior malware analyst at Bitdefender, said that their antivirus did catch the RCS sample some time ago, via behavioral detection. Other solutions may also be able to detect the threat in a similar way.
Late last week, Guarnieri tweeted the result of a VirusTotal analysis for a newer sample of RCS spyware and the results were also disheartening: only two engines labeled the file as a threat.
The RCS sample tested by the researcher on Sunday was particularly evasive, as it was disguised as a popular bookmark manager called Linkman, and it also benefited from a valid digital signature.
In a tweet late last week, Outertech, makers of Linkman, warned its customers to check if the name of the publisher matches theirs when the bookmark manager is installed. The malicious version relied on a certificate issued for an entity called Jagdeependra.
There you go, another HackingTeam sample uploaded more than a month ago. So much green. https://t.co/yKUHOKZqKp pic.twitter.com/5DB8usFi6w
— Claudio (@botherder) November 26, 2014
Just saying. I don't know, do I need to try them all? #HackingTeam pic.twitter.com/l64iwuxdgH
— Claudio (@botherder) November 26, 2014
New undetected HackingTeam sample just uploaded on VirusTotal https://t.co/CI3VD35iiL disguised as @outertech Linkman pic.twitter.com/01aDSO9SoA
— Claudio (@botherder) November 23, 2014
 14 DAY TRIAL //
14 DAY TRIAL //